 Facebook continues to demonstrate their commitment to making sure that people can access Facebook from whatever networks they may be on – and particularly new IPv6-based networks. Not only is Facebook moving to an IPv6-only internal network, but now comes word that their iOS mobile applications, both the regular Facebook app and also the Facebook Messenger app, can work perfectly fine on an IPv6-only network.
Facebook continues to demonstrate their commitment to making sure that people can access Facebook from whatever networks they may be on – and particularly new IPv6-based networks. Not only is Facebook moving to an IPv6-only internal network, but now comes word that their iOS mobile applications, both the regular Facebook app and also the Facebook Messenger app, can work perfectly fine on an IPv6-only network.
The information was relayed by Facebook’s Paul Saab in, of course, the IPv6 Group on Facebook. Back on December 2, Paul wrote:
The most recent release of the Facebook iOS app works on IPv6-only networks. The interesting thing in making this all work, is the example Reachability code that apple released really only showed how to implement it for IPv4 or hostnames, but using a hostname was broken if you were on an IPv4 only network and the hostname was dual stacked. Anyway, the main app is now fixed and our Messenger application will be updated soon to also have the fix.
And late last night he posted:
The FB Messenger was released and now supports IPv6-only networks
As the discussion thread indicates, the Android versions of the two apps should also work on IPv6-only networks but there are currently issues with Android devices in general working on IPv6-only networks.
The key point here is that as some network operators are now deploying IPv6-only networks because of a lack of IPv4 addresses. Consider the case of T-Mobile USA. Facebook’s applications will work fine and give the best possible user experience on those IPv6-only networks. Some of these new IPv6-only networks, such as those in the mobile space, use technologies such as 464XLAT to enable IPv4-only applications to still work. BUT… any such translation technologies do add complexity and introduce some degree of latency (which might be quite tiny, but still there).
Facebook is avoiding all of that by making sure that their mobile applications work well in IPv6-only networks.
Those apps will work over native IPv6 networks to connect back to Facebook’s IPv6 data centers. Without needing to pass through some IPv4 gateway or translation tool, the apps should provide the fastest and simplest connections – which means a better experience for users.
Now, the Facebook applications also work fine in a “dual-stack” mixed IPv6/IPv4 network. They have for quite a long time now. But Facebook has now tested these apps on networks without IPv4 – and that is a difference.
Congratulations to Paul Saab and the rest of the team there at Facebook for taking this step – and we hope that other mobile application developers will see this and consider testing their applications on IPv6-only networks as well.
As we run out of IPv4 addresses and have to look at IPv6-only networks with some kind of IPv4 translation on the edge… the best possible user experience is going to be with those applications and services that can avoid all of the IPv4 translation and work completely over IPv6.
P.S. If you would like to get started with moving your application or service to IPv6, please visit our Start Here page for pointers on how to begin!

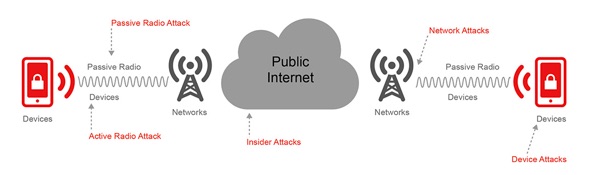



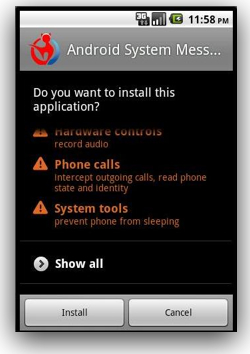 News out of the CA Security Advisor Blog today is that
News out of the CA Security Advisor Blog today is that 