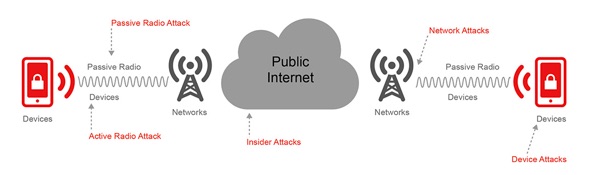
Verizon Wireless this week did something that initially seemed quite impressive – they launched “Voice Cypher”, an app available for iOS, Android and Blackberry that promises secure end-to-end encryption. It uses VoIP and is an “over-the-top” (OTT) app that works on any carrier. If you read the marketing material on their web site, it all sounds great! Indeed their “Learn More” page has all the right buzzwords and security lingo – and says quite clearly: Voice Cypher provides end-to-end encryption between callers, even if the call crosses over multiple networks.” They include the requisite network diagram that shows how it protects against all threats:
It turns out there’s just one small little detail … as reported by BloombergBusinessweek, the app comes complete with a backdoor so that Verizon could decrypt the phone calls if requested to do so by law enforcement!
As the Businessweek article states:
Cellcrypt and Verizon both say that law enforcement agencies will be able to access communications that take place over Voice Cypher, so long as they’re able to prove that there’s a legitimate law enforcement reason for doing so.
Unfortunately, in this post-Snowden era I don’t know that many of us put a great amount of trust in our governments to only access communications with a “legitimate law enforcement reason”. Or perhaps the concern is that what gets classified as “legitimate” can be widely construed to mean almost anything.
The article does point out that Verizon is bound by CALEA to provide lawful intercept to the phone networks, but points out an interesting caveat that Verizon could have used:
Phone carriers like Verizon are required by U.S. law to build networks that can be wiretapped. But the legislation known as the Communications Assistance for Law Enforcement Act requires phone carriers to decrypt communications for the government only if they have designed their technology to make it possible to do so. If Verizon and Cellcrypt had structured their encryption so that neither company had the information necessary to decrypt the calls, they would not have been breaking the law.
A Verizon Wireless representative indicated that they believe government agencies looking for ways to protect sensitive information may be customers of this service, as may be corporate customers concerned about leaking private information.
But… as we continue to hear more and more information about the massive amount of pervasive monitoring and surveillance by government agencies from many different governments around the world, you do have to wonder how safe those agencies and companies will feel with a “secure” solution that already comes with a backdoor. The problem with a known backdoor is that even if you may trust Verizon Wireless to only allow legitimate law enforcement access… how do you know that some attacker may not be able to penetrate that backdoor? The “secure end-to-end encryption” isn’t entirely secure.
Given that the service has a higher price tag of $45 per month per device, I do wonder how many businesses or agencies will actually embrace the service.
On reading about this Voice Cypher service, it certainly sounds quite interesting. We need more secure voice solutions out there – and it’s very cool that Verizon Wireless is delivering this as an OTT mobile app that will work across different carriers.
It’s just too bad that it’s not truly “secure end-to-end”. ![]()
P.S. I also recorded an audio commentary on this same topic.

 News out of the CA Security Advisor Blog today is that
News out of the CA Security Advisor Blog today is that 