Just a guy in Vermont trying to connect all the dots...
Author's posts
Oct 04
The DANE Protocol – DNS-Based Authentication of Named Entities
If you connect to a website using a “secure” connection over TLS/SSL, how do you know you are using the correct TLS/SSL certificate?
You may see the “lock” icon in your web browser, but are you sure that you are connecting all the way to the website using the correct TLS certificate? It is in fact quite possible – and quite common – for a firewall or other device in your network path to terminate your TLS connection with a website and then re-create a TLS connection from the device to your browser. You think you have a secure, encrypted connection to your bank, for instance, but in fact your connection has been intercepted and the firewall or other device is able to see, and potentially record, all your interaction with the web site.
With DNSSEC now being deployed, a new protocol has emerged called “DANE” (“DNS-Based Authentication of Named Entities“) that allows you to securely specify exactly which TLS/SSL certificate a browser should use to connect to your site. If a web browser supporting DANE detects that it is NOT using the specified certificate, it can warn you that your connection is insecure… even though you see a “lock” icon.
DANE is defined in RFC 6698 and over the next few months we will be adding more tutorials and document to this site to help you understand both how DANE helps make the Internet more secure and also how you can get started either publishing TLSA records for your domain – or using DANE within your application. Note that DANE is not just for websites. People are already looking at how DANE can be used to secure email, VoIP and other web services.
For an explanation of the DANE protocol, watch this interview with Warren Kumari, co-chair of the DANE Working Group within the IETF:
[Additional screencast to be inserted here explaining how DANE works.]
Another good introduction to DANE is an IETF Journal article published in October 2011 titled “DANE: Taking TLS Authentication to the Next Level Using DNSSEC“. In the article, Richard Barnes explains why DANE is needed, outlines how it works, digs into some of the challenges with DANE implementation and provides a good number of links for more information.
Content Providers
[This section will explain to website owners/operators and providers of other services how they can publish TLSA records to make their sites more secure.]
Application Developers
The following libraries are in the process of adding support for the DANE protocol:
- dnspython – the development version of dnspython found on Github has had support for TLSA records added to the code base. This is not yet available in a formal release.
- ldns – an upcoming release of ldns will provide support for DANE (this page will be updated when the release occurs).
Other resources for developers:
- DANE Test Sites – If you are adding DANE support to your application and wish to test out how well it works, the sites on this page are early supporters of the protocol and can be used in your testing.
Getting More Involved
If you would like to get more involved in the development of the DANE protocol and supporting documentation, you can:
- Read the RFCs and other documents associated with DANE
- Understand the DANE working group charter
- Join the DANE mailing list
Oct 02
How Do We Measure DNSSEC Deployment?
 How do we measure the actual deployment of DNSSEC? How can we know how many domain name holders have signed their zones with DNSSEC? How can we find out how many ISPs have deployed DNSSEC-validating resolvers? How do we count how many applications or operating systems have built-in support for DNSSEC validation?
How do we measure the actual deployment of DNSSEC? How can we know how many domain name holders have signed their zones with DNSSEC? How can we find out how many ISPs have deployed DNSSEC-validating resolvers? How do we count how many applications or operating systems have built-in support for DNSSEC validation?
At first glance, some of these would appear to be simple questions to answer – “well, can’t you just count up the number of DS records in a top-level domain?” But the reality is that it’s not quite that simple. There are sites providing DNSSEC deployment statistics and some TLDs are making DNSSEC usage available… but that’s not true across the board. And the validation question is quite difficult due to the distributed and decentralized nature of the Internet. We recently wrote about some work Verisign Labs is undertaking to measure validation, but that work is just beginning.
The APNIC Experiment
So we were delighted to see the post, “Counting DNSSEC” and accompanying presentation from Geoff Huston and George Michaelson at APNIC Labs where they dug into this DNSSEC measurement issue in a unique way. As Geoff writes, they set out to look at these questions:
- How many zones are DNSSEC signed?
- How many DNS queries are DNSSEC-validated?
- How many DNS resolvers are DNSSEC-capable?
- How many users are using DNSSEC-aware DNS resolvers?
But rapidly concluded that these precise questions were difficult to answer – and so they decided to look a bit more broadly at these questions:
- What proportion of DNS resolvers are DNSSEC-capable?
- What proportion of users are using DNSSEC-validating DNS resolvers?
- Where are these users?
Their measurement technique was to use advertisements in web browsers displayed through an advertising network. They used a flash-based ad that made multiple DNS requests without user intervention, i.e. the user didn’t have to click on the ad – just the action of displaying the ad triggered the measurements.
They ran the test from September 10-17, 2012, and observed 57,268 unique IP addresses requesting the DNS records. Some of the conclusions were interesting:
- 4% of DNS resolvers performed DNSSEC validation
- 9% of end-client systems were using a DNSSEC-validating resolver
Their post goes through all this in great detail and provides a much more thorough explanation than I can do here.
They then went on to look at where the users were coming from and provide charts segmenting their data in multiple different ways. They summarized all of this in a presentation to the recent RIPE 65 event complete with charts showing the validation by country. I’d highly recommend you take a look at that presentation as it provides an excellent view into all this data.
As with any survey like this, you can always wonder about the distribution of people seeing the displayed ad. My first thought was that as I browse with Flash disabled by default I would never have triggered their measurement had it been displayed on my screen. Similarly many mobile devices might not execute Flash, notably Apple devices, and so it would miss those users.
But even with those caveats, this is an excellent piece of work as an attempt to perform some basic measurements. Geoff notes at the end of the post that they’ll perform another look at DNSSEC deployment in a few months time, and we’re very much looking forward to seeing what difference they’ll measure in that next look.
What Else Can Be Done?
Beyond this work, we are still thinking a great bit about what else can be measured. For instance, can we as an industry develop:
- a count of registrars supporting DNSSEC by allowing upload of DS records?
- a count (or %) of DNS hosting providers providing automated DNSSEC signing?
- a % of ISPs providing validating name servers?
- a % of signed second-level domains?
On this last point, there are great examples already out there including the PowerDNS stats for .NL and other domains, the Verisign Labs scoreboard for .COM/.NET/.EDU and the NIST statistics for the US Gov’t and industry, but it would be even better if we could aggregate this information and also obtain that information for other TLDs.
How can we best measure the deployment of DNSSEC? It’s an interesting question… do you have any thoughts about other methods and mechanisms?
Oct 02
Slides: How The Hidden Secret of TCP/IP Affects Real-time Communications
This presentation (slides available) really hits a number of key points about where we are at now:
In particular I was struck by his slides 24-28 that strike the same theme I've been writing about across multiple blogs, namely the way we are reversing the "open Internet" trend and retreating back inside walled gardens of messaging:
He goes on to walk through what happened with SIP and how the protocol evolved - and evolved away from interoperability. His conclusion is that we as customers need to take back control, avoid vendor lock-in and demand interoperability.
He also points people over to his "SIP 2012" effort where he is undertaking to compile a list of what really defines "SIP" in 2012, i.e. more than just RFC 3261. (I'll note he's looking for feedback on these ideas.)
All in all an excellent presentation... and yes indeed we all collectively do need to "WAKE UP" and demand better solutions!
If you found this post interesting or useful, please consider either:
- following me on Twitter;
- adding me to a circle on Google+;
- subscribing to my email newsletter; or
- subscribing to the RSS feed
Oct 01
Video from CO ISOC: IPv6: What is it, why do I need it, and how do I get it?
What is IPv6 all about? Why do you need it? How do you get it? These are the questions a recent event hosted by the Colorado (US) chapter of the Internet Society on August 28, 2012, sought to answer. The session began with a keynote by Scott Hogg, Director,Technology Solutions, Global Technology Resources (GTRI) and then was followed by a panel including:
- Jeff Doyle, President, Jeff Doyle and Associates
- Chris Grundemann, Network Architect, CableLabs
- Cricket Liu, VP, Architecture & Technology,Infoblox
- Shannon McFarland, Principal Engineer, Corporate Consulting Engineering Group, Cisco
- Scott Hogg, Director,Technology Solutions, Global Technology Resources (GTRI)
More information and bios of the presenters can be found at: https://coisocipv6.eventbrite.com/
The session itself is available on YouTube and comes in around 1 hour and 46 minutes:
Oct 01
FIR #671 – 10/01/12 – For Immediate Release
Sep 28
U.S. White House Website Now On IPv6
Given that the IPv6 mandate for US federal government agencies came from the Obama administration, a few people noted in recent days that the White House website was not available over IPv6 and indeed it was not listed in yesterday’s run of NIST’s list of US government IPv6-enabled sites.
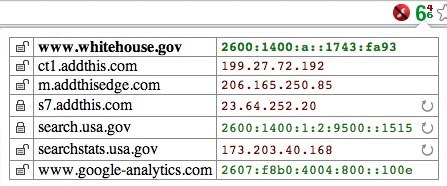
This morning, though, brings the news that www.whitehouse.gov is now accessible over IPv6. A quick “dig aaaa www.whitehouse.gov” shows these results:
;; ANSWER SECTION: www.whitehouse.gov. 2441 IN CNAME www.whitehouse.gov.edgesuite.net. www.whitehouse.gov.edgesuite.net. 216 IN CNAME www.eop-edge-lb.akadns.net. www.eop-edge-lb.akadns.net. 61 IN CNAME a1128.dsch.akamai.net. a1128.dsch.akamai.net. 7 IN AAAA 2600:1400:a::1743:fa93 a1128.dsch.akamai.net. 7 IN AAAA 2600:1400:a::1743:fa78
… which indicate that the site is apparently one of the ones that we mentioned yesterday that Akamai would be enabling via IPv6.
A visit to the White House site using the very cool IPvFoo extension for Google Chrome also shows this graphically:
I would note that the image shows the standard challenge of modern websites that they are comprised of many different components that load dynamically, some of which are available over IPv6 and some still only over IPv4. The key point, though, is that www.whitehouse.gov is accessible over IPv6.
Kudos to the White House team and Akamai for making the site available over IPv6. We look forward to seeing how many more US government sites come online throughout today and over the weekend.
Can we help you get started with IPv6?
P.S. If you like the idea of this IPvFoo extension but are a Firefox user, there is a similar add-on called IPvFox.
Sep 27
With September 30 Deadline Looming, US Government Enables IPv6 For Hundreds Of Websites
This Sunday, September 30, 2012,  marks the deadline for US federal government agencies to make their public web services available over IPv6 according to an Obama administration mandate established two years ago.
marks the deadline for US federal government agencies to make their public web services available over IPv6 according to an Obama administration mandate established two years ago.
The reality is that all US agencies will not make the deadline which, somewhat predictably, has generated media stories slamming the government for not moving fast enough.
But that’s the easy path to take, particularly in an election season when attacking the government is basically a sport in the U.S. However, when you dig a bit deeper, the story is really quite an amazing accomplishment. Consider these points:
- Most agencies did not have a plan for deploying IPv6 publicly prior to the mandate being established two years ago. Earlier IPv6 mandates (in 2008) had focused on making IPv6 available on agencies’ network backbones, and some agencies did go further with IPv6 deployment plans but most had not progressed farther.
- The IPv6 mandate did NOT include any additional funding. There was no magic pot of “IPv6 money.” Agencies were simply directed to make it happen.
- Agencies already had existing contracts with network operators and other vendors. These needed to be modified to include IPv6.
- The US government is a massively distributed, “loosely coupled,” large enterprise with a huge number of discrete entities with different policies, administrations, processes, networks, IT infrastructures, etc.
In light of all those points, the fact that per NIST’s recent snapshot close to 50% of the US government domains have made progress on IPv6 is quite remarkable:
NIST’s list of US government websites [1] currently shows 326 sites available over IPv6 and in a recent Network World article Carolyn Duffy Marsan quoted Christine Schweickert of Akamai saying that they will have “an additional 300 to 400 federal Websites dual-stacked between now and Friday the 27th” so we can expect to see that number grow much higher in the next few days. (To understand how Akamai is helping, view our video about how content delivery networks (CDNs) can IPv6-enable websites.)
Reading the list of US government sites is quite fascinating as there are sites there that I had no idea even existed:
NIST also has a detailed page showing details of the USG sites being tracked for IPv6 deployment. The page contains the following information:
- The number of network interfaces configured for IPv4 and IPv6. Note the nuance here – this graph is not the number of web sites but rather the number of servers that are enabled for IPv6. Those servers could of course host multiple sites.
- IPv6 deployment trends over time. The growth is great to see.
- Deployment details for each site being tracked.
This last section is quite interesting as it shows the details being the snapshot graph I included above. Here you see precisely which services agencies have turned on and which are not yet available:
You can also click on the name of any agency to get detailed statistics for that particular agency. (NIST also provides another page showing IPv6 deployment by agency that breaks down the IPv6-enabled domains by individual agencies.)
There’s obviously a bit more “red” on that chart than they’d like, but it’s encouraging to see the amount of green appearing as you scroll down. As noted in the Network World article, this is more progress at a government level than most countries have made. And, if you look at the stats NIST is tracking for the broader industry and universities, the US government is well ahead of both sectors in IPv6 deployment:
We are looking forward to checking the statistics on Monday, October 1, to see how many agencies did in fact meet the deadline. In the meantime we certainly commend those US government agencies that have made the leap and enabled IPv6.
P.S. Want to learn more about how you can get started with IPv6, check out our online resources to help?
[1] This page is called “World IPv6 Launch Sites” as that was what it was originally created for, but NIST has continued updating it as new sites come online.
Sep 26
Alec Saunders Is A Rock Star In RIM’s Strange New Blackberry 10 Video
Sometime after my friend Alec Saunders joined RIM last year as their VP of Developer Relations, I said to someone that while I admittedly did view his new mission as somewhat akin to tilting at windmills, he was perhaps just the kind of "rock star" that RIM needed. A very passionate and dynamic presenter... a very charismatic leader who could rally people... a creative guy with a theatre background... someone who thinks differently...
... never in my wildest ideas did I expect that we would be seeing Alec AS an actual "rock star" in a music video! But yes indeed, here he is with two other VPs from RIM in a remake of the famous REO Speedwagon song. (Alec is the main singer.)
Unbelievable.
My speechlessness soon gave way to laughter ... and appreciation for them for doing something rather different. If they were looking for a way to be "remarkable" and memorable, they found it.
Now, somewhat predictably, some of the tech press are calling this an act of sheer desperation and I'm seeing comments in social networks calling it "painful" and "cringeworthy."
But that's the point, really... the video is getting people talking about Blackberry!
Even me, who hasn't really written about RIM and Blackberry here since, oh, last year shortly after he joined RIM. :-)
The video is over the top... I did cringe a couple of times as they twisted lyrics to fit the tune. But it made me smile. And laugh. And I'll remember it!
Will it attract new developers to the BB10 platform? Will it keep existing developers staying loyal to the platform?
I don't know. They have a huge uphill battle to fight. But hey, at least this was something fun and different!
Kudos to Alec and all the folks at RIM for what was obviously a great amount of time, energy and talent into doing something definitely unique!
And here's the full video for those who want the experience:
If you found this post interesting or useful, please consider either:
- following me on Twitter;
- adding me to a circle on Google+;
- subscribing to my email newsletter; or
- subscribing to the RSS feed
Sep 25
Video: What Is WebRTC/RTCWeb All About? How Does WebRTC Work?
I recently wrote about some of the larger issues of how WebRTC will disrupt telecom, but in this video, "RTCWeb Explained", Cullen Jennings, one of the co-chairs of the IETF's RTCWEB working group, dives down into the technical details to explain how it all works and what the various different components of of the solution are. I particularly like how Cullen covered some areas like "identity" that I haven't seen stressed as much in other pieces about WebRTC. The video comes in at about 39 minutes and is well worth viewing:
For more information, I've put together a page about the broader WebRTC / RTCWEB initiative with links to relevant resources.
If you found this post interesting or useful, please consider either:
- following me on Twitter;
- adding me to a circle on Google+;
- subscribing to my email newsletter; or
- subscribing to the RSS feed
Sep 24
Got an IPv6-enabled app? Enter this Application Contest for a 10,000 Euro prize!
 Have you created an application that does something unique or interesting with IPv6? Or makes use of new capabilities that come with IPv6? Or have you expanded an existing application so that it now works with IPv6?
Have you created an application that does something unique or interesting with IPv6? Or makes use of new capabilities that come with IPv6? Or have you expanded an existing application so that it now works with IPv6?
If so, consider entering the International Application Contest 2012 sponsored by the IPv6 German Council. As noted on the page about applications, the contest is open to “companies, groups or individuals of any nationality” and has a first prize of 10,000 Euros! The deadline to apply is October 24, 2012.
Do note the judging criteria listed further down the page:
- What contribution is made to create a new Internet experience?
- How will the contribution promote and spread IPv6, the next Internet protocol?
It’s great to see contests like this out there – and we look forward to seeing what applications are submitted.
Want to get started with your application? Check out our suggestions for developers!