Just a guy in Vermont trying to connect all the dots...
Author's posts
Jan 01
Happy New Year!
 Happy New Year! After a fantastic 2012 we’re looking forward to bringing you even more real-world deployment information this year about IPv6, DNSSEC and now our latest topic of Routing Resiliency / Security.
Happy New Year! After a fantastic 2012 we’re looking forward to bringing you even more real-world deployment information this year about IPv6, DNSSEC and now our latest topic of Routing Resiliency / Security.
The question is… what will you do in 2013?
Will you deploy IPv6 in your network? Will you sign your domains with DNSSEC? Or deploy DNSSEC-validating resolvers in your network? Will you look at ways to make your routing infrastructure more resilient?
The second question is… how can we help you?
What can we do to help you deploy IPv6 or DNSSEC? How can we help you better secure your routing?
Please let us know… we want to help you makeyour networks stronger, more flexible and more secure… and in doing so make the open Internet just that much better!
Dec 31
Will Your New Year’s Resolutions Include IPv6? DNSSEC? Routing?
 It’s the last day of 2012… are you making resolutions for the New Year?
It’s the last day of 2012… are you making resolutions for the New Year?
If so, how about one of these:
- Get IPv6 fully deployed in our network.
- Set up an IPv6 test network in my home or office.
- Read a book about IPv6.
or
- Sign at least one of my domains with DNSSEC.
- Deploy DNSSEC-validating resolvers in my network.
- Understand what DANE is all about.
or
- Read one of these reports to better understand the Internet’s routing infrastructure.
- Attend one of Deploy360′s ION Conferences in 2013.
- Send Deploy360 some feedback about what you’d like to see them add to their site.
or
- Join the Internet Society as a member and help keep the Internet open for everyone.
- Follow us on Twitter, Facebook, Google+ and other social networks
- Tell your friends about IPv6 or DNSSEC
Or, of course, you could always go with:
- Post more kitten videos online, because clearly there aren’t enough
What will your resolution be for 2013?
Photo credit: Lori Ann of MamaWit on Flickr.
Dec 31
FIR #684 – 12/31/12 – For Immediate Release
Dec 28
Weekend Project: Add DNSSEC Validation to an OpenWRT WiFi Device
 Looking for a weekend project? Do you use a WiFi access point based on OpenWRT?
Looking for a weekend project? Do you use a WiFi access point based on OpenWRT?
If so, here are some quick instructions about how to install the Unbound DNS resolver that supports DNSSEC validation into OpenWRT. What this will do is change the DNS resolver in your access point to start performing DNSSEC validation… so as more domains get signed you’ll be able to know that you are, in fact, getting to the correct domain. Plus, with DNSSEC validation available you’ll be able to start playing around with very cool new technologies like the DANE protocol… who knows what you’ll be able to do with it!
The great thing is that it turns out to be a trivial process, which is great to see!
P.S. While you’re hacking on your devices, check out some of the other DNSSEC tools we are listing…
Dec 27
Youth Curling Open House – Fri, Dec 28, 1-3pm – Petersham, MA
Youth Curling Open HouseCurling is a fun team sport that is open to pretty much anyone to be able to play. I play in an adult league on Tuesday nights and my 10-year-old daughter (pictured) plays in the youth curling on Saturday mornings. It's about a 45-minute drive for us from Keene, NH, but it's worth it to play on good ice and learn the sport.
Friday, December 28, 2012 from 1-3pm
Petersham Curling Club, Petersham, MA
You are welcome to come by tomorrow and try it out. The open house is free and directions are available on the Petersham Curling Club website.
If you can't make it tomorrow but are interested in staying up on future events like this, we also have a Facebook page for the Petersham Youth Curling that you can "Like" and stay connected.
We'd welcome any youth who would like to join us on the regular Saturday mornings... it's a great amount of fun!
Dec 27
Sledding at Robin Hood Park
|
via YouTube Capture. |
From:
Dan York
Views:
27
     0
ratings | |
| Time: 00:23 | More in People & Blogs |
Dec 26
IPv6 Kongress 2013 Call For Papers Deadline of January 20
 The IPv6 Kongress 2013 is scheduled for June 6 and 7 in Frankfurt, Germany, and the program committee there has issued a call for papers seeking presenters on IPv6 topics. Some of the session topics they are seeking include:
The IPv6 Kongress 2013 is scheduled for June 6 and 7 in Frankfurt, Germany, and the program committee there has issued a call for papers seeking presenters on IPv6 topics. Some of the session topics they are seeking include:
- IPv6 und Smartphones respektive Tablets
- IPv6-spezifische Sicherheitsprobleme
- Einführungsverfahren in Firmennetzen
- Privacy und Datenschutz
- Praxisrelevante Unterschiede zwischen altem und neuem Protokoll
- IPv6 in Embedded Systems
- IPv6-Goodies – was uns ohne IPv6 bislang alles entgangen ist …
Obviously, the conference is in German… although “IPv6-Goodies” is probably understandable in any language! ![]()
The deadline to submit a proposal is January 20, 2013. More info on the call for papers page.
Dec 24
Google+ Available Over IPv6
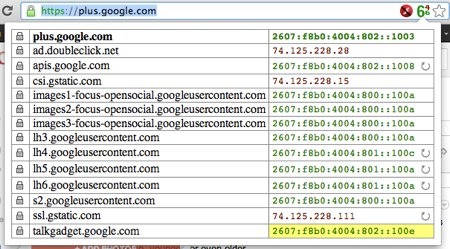 For those of us who are fans of Google+ and also IPv6, we were pleased to note that Google+ is accessible over IPv6.
For those of us who are fans of Google+ and also IPv6, we were pleased to note that Google+ is accessible over IPv6.
Now, it may have honestly been this way for a while, but a Google+ update from Wes Hardaker made me pay attention to this fact. Using the outstanding IPvFoo extension for Google Chrome (similar to the IPvFox add-on for Firefox), I could easily see that yes, indeed, my connection to Google+ was over IPv6.
It’s always interesting to click on the IPvFoo icon in my browser address bar and see what is not coming to me over IPv6, and in this case it seems to be ads being served by DoubleClick and whatever content is coming from gstatic.com:
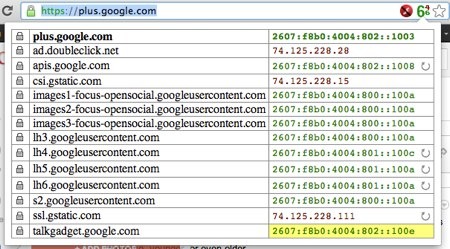
However, everything else is coming in over IPv6!
Now, sometimes that does change, I’ve noticed, but I expect that is simply a result of Chrome’s “Happy Eyeballs” implementation where it may sometimes find IPv4 to be faster than IPv6.
All in all it’s good to see… now we have both Google+ and Facebook accessible over IPv6. Now we just need to get Twitter over IPv6!
P.S. While you’re over on Google+ checking this out, how about adding our Deploy360 page to a circle and giving us a +1? We’d love to interact with you over there.
Dec 24


