Just a guy in Vermont trying to connect all the dots...
Author's posts
Dec 16
Facebook’s iOS Apps Now Work On IPv6-Only Networks
 Facebook continues to demonstrate their commitment to making sure that people can access Facebook from whatever networks they may be on – and particularly new IPv6-based networks. Not only is Facebook moving to an IPv6-only internal network, but now comes word that their iOS mobile applications, both the regular Facebook app and also the Facebook Messenger app, can work perfectly fine on an IPv6-only network.
Facebook continues to demonstrate their commitment to making sure that people can access Facebook from whatever networks they may be on – and particularly new IPv6-based networks. Not only is Facebook moving to an IPv6-only internal network, but now comes word that their iOS mobile applications, both the regular Facebook app and also the Facebook Messenger app, can work perfectly fine on an IPv6-only network.
The information was relayed by Facebook’s Paul Saab in, of course, the IPv6 Group on Facebook. Back on December 2, Paul wrote:
The most recent release of the Facebook iOS app works on IPv6-only networks. The interesting thing in making this all work, is the example Reachability code that apple released really only showed how to implement it for IPv4 or hostnames, but using a hostname was broken if you were on an IPv4 only network and the hostname was dual stacked. Anyway, the main app is now fixed and our Messenger application will be updated soon to also have the fix.
And late last night he posted:
The FB Messenger was released and now supports IPv6-only networks
As the discussion thread indicates, the Android versions of the two apps should also work on IPv6-only networks but there are currently issues with Android devices in general working on IPv6-only networks.
The key point here is that as some network operators are now deploying IPv6-only networks because of a lack of IPv4 addresses. Consider the case of T-Mobile USA. Facebook’s applications will work fine and give the best possible user experience on those IPv6-only networks. Some of these new IPv6-only networks, such as those in the mobile space, use technologies such as 464XLAT to enable IPv4-only applications to still work. BUT… any such translation technologies do add complexity and introduce some degree of latency (which might be quite tiny, but still there).
Facebook is avoiding all of that by making sure that their mobile applications work well in IPv6-only networks.
Those apps will work over native IPv6 networks to connect back to Facebook’s IPv6 data centers. Without needing to pass through some IPv4 gateway or translation tool, the apps should provide the fastest and simplest connections – which means a better experience for users.
Now, the Facebook applications also work fine in a “dual-stack” mixed IPv6/IPv4 network. They have for quite a long time now. But Facebook has now tested these apps on networks without IPv4 – and that is a difference.
Congratulations to Paul Saab and the rest of the team there at Facebook for taking this step – and we hope that other mobile application developers will see this and consider testing their applications on IPv6-only networks as well.
As we run out of IPv4 addresses and have to look at IPv6-only networks with some kind of IPv4 translation on the edge… the best possible user experience is going to be with those applications and services that can avoid all of the IPv4 translation and work completely over IPv6.
P.S. If you would like to get started with moving your application or service to IPv6, please visit our Start Here page for pointers on how to begin!
Dec 15
Moving My Various Web Sites To Responsive Design To Be Mobile-Friendly
Today I made on change on this "DanYork.com" site to move it to a new theme that uses "responsive design" so that it will look good on a mobile device as well on a large screen. I've been wanting to do this for quite some time because any of a zillion reports out there will tell you that an increasing majority of users are viewing websites on their mobile devices. I can just see that in my own behavior where I use my iPhone or iPad for viewing so many sites.
The challenge I have is that this site, and my other major personal blog sites, are all still hosted on TypePad, one of the early blog hosting providers where I started writing back in 2005 or so. Some year I'd love to consolidate them onto one of the other hosted sites where I run WordPress... but the amount of work to do so is quite substantial given the hundreds upon hundreds of posts between my various sites. Some day...
Meanwhile, I figured out enough about TypePad's one responsive design theme to be able to move this site over. At some point over my holiday vacation I'd like to move these two over to a responsive theme:
They are where the bulk of my personal writing occurs. The challenge with any move to a new theme on TypePad is that you need to rebuild the menus, sidebars, etc., so it does take a bit of time.
I also want to move my writing aggregation site to a responsive theme:
That site is hosted on WordPress and so there are many options... I just have to find one that I like and spend the time configuring it.
Most of my other WordPress-hosted sites already are responsive, including:
Out of my various websites where I write that will really just leave CircleID, where I have no control over the formatting, and my 7 Deadliest UC Attacks site that is also still hosted by TypePad. If I have the time, I'll probably just move that one during the migration of my DisTel and DisCon sites.
And then, of course, there is my Deploy360 site at work... which is a MUCH bigger challenge that will be dealt with sometime in 2015...
The end goal will be that people will be able to read my writing with ease on whatever platform they use - mobile phone, tablet, desktop... or anything else.
Stay tuned...
Dec 15
FIR #786 – 12/15/14 – For Immediate Release
Dec 15
Indonesia And Vanuatu Sign .ID and .VU With DNSSEC
 We were very pleased to learn this morning that both Indonesia’s .ID and Vanuatu’s .VU country-code top-level domains (ccTLDs) had DS records uploaded to the root zone of DNS over the weekend. What this means is that they have both entered the fourth of five deployment stages that we track as part of the DNSSEC Deployment Maps.
We were very pleased to learn this morning that both Indonesia’s .ID and Vanuatu’s .VU country-code top-level domains (ccTLDs) had DS records uploaded to the root zone of DNS over the weekend. What this means is that they have both entered the fourth of five deployment stages that we track as part of the DNSSEC Deployment Maps.
At some point soon, people who have registered domains under .ID and .VU should be able to upload their own DNSSEC records and be able to obtain the higher level of security and trust that comes with having their domain signed with DNSSEC. We don’t yet know when the registries for .ID and .VU will start accepting DS records from registrants, but hopefully at some point soon.
Given that the records were entered into the root zone of DNS after I had finished updating the database on Friday for the DNSSEC Deployment Maps that were distributed this morning, I took the unusual step of re-generating the maps today after a quick database update. Subscribers to the public dnssec-maps mailing list have all received a second set of maps for today. Normally I might have just waited for next week but given Indonesia’s size it adds a nice bit of green to the Asia Pacific map and I wanted that to be shown.
With these two ccTLDs having their DS record in the root zone, this brings us to 97 of the 247 ccTLDs that we track in our database being signed with DNSSEC. (There are also .EU and .SU which we consider more “regional” TLDs (and are both signed), but other lists count as ccTLDs, so you could say that we show 99 of 249 being signed.) Given that most of the generic TLDs are signed and all the new gTLDs MUST be signed when they launch, the remaining 150 unsigned ccTLDs are the major area where attention will be focused over the next while in terms of getting TLDs signed. ICANN’s DNS team is spending a good bit of time traveling to many of these countries to help them get their ccTLDs signed and operational.
Congratulations to the teams at .ID and .VU for getting their domains signed and linked in to the DNSSEC global “chain of trust”. We look forward to learning that those two ccTLDs become “Operational” and second-level domains can begin uploading DNSSEC records soon.
Note – if you would like to learn more about how you can get started with DNSSEC, please visit our Start Here page to find resources tailored to your role or type of organization.
Dec 15
Two Weeks In… How Is A Blog Post A Day Doing? #Finish2014Strong
 So, two weeks after saying I would write at least one blog post a day (and talking about that) for all of December 2014, how am I doing?
So, two weeks after saying I would write at least one blog post a day (and talking about that) for all of December 2014, how am I doing?
Well... so far so good.
- I posted at least once on the Deploy360 site every work day.
- I did put something up on my personal sites every day so far.
- I recorded a new "The Dan York Report" podcast on 10 of the 14 days.
I've had a serious cold/cough that made for really poor audio... so on some of the worst days I skipped it. I didn't think it made sense to record a poor-quality audio podcast just for the sake of saying I did it.
In fact, I'm honestly surprised how much I did write, given how foggy my head has felt and how most days it has seemed like I'm moving through molasses.
Now... the question will be whether I can continue this through the remaining days that include holidays and vacation time!
Here's the list of the month so far:
Monday, December 1
Deploy360 Programme:
Personal Sites:
- Disruptive Conversations: A Blog Post A Day For December 2014 – #Finish2014Strong
- Migrating Apps To IPv6: Cyber Monday: 50% Off Ebook of “Migrating Applications to IPv6″
- Seven Deadliest Unified Communications Attacks: Can You Please Rate or Review 7 Deadliest UC Attacks On O’Reilly’s Site?
- Seven Deadliest Unified Communications Attacks: <em>Cyber Monday: 50% Off Ebook of "Seven Deadliest Unified Communications Attacks"
The Dan York Report audio podcast:
Other:
- FIR podcast #784 – 12/1/14 - (includes my weekly report into FIR)
Tuesday, December 2
Deploy360 Programme:
Personal Sites:
- Disruptive Telephony: How To Test Firefox Hello, Mozilla’s New WebRTC Video Call Service
The Dan York Report audio podcast:
Wednesday, December 3
Deploy360 Programme:
Personal Sites:
- Disruptive Telephony: Initial Thoughts On "Wire", The New Communication App From Ex-Skypers
The Dan York Report audio podcast:
Thursday, December 4
Deploy360 Programme:
DNSSEC Deployment Initiative:
Personal Sites:
- CircleID: Call For Participation – ICANN 52 DNSSEC Workshop on 11 Feb 2015 In Singapore
- Disruptive Telephony: More Observations About The "Wire" App
The Dan York Report audio podcast:
Friday, December 5
Deploy360 Programme:
Personal Sites:
- Disruptive Telephony: How To Add An Emoji Character To Your Name In The Wire App
The Dan York Report audio podcast:
- (no podcast - too sick)
Saturday, December 6
Deploy360 Programme:
- (no post)
Personal Sites:
The Dan York Report audio podcast:
Sunday, December 7
Deploy360 Programme:
- (no post)
Personal Sites:
- Dan York.com: In Every Action We Take, We Create The World We Want To Live In (And yes, this one was a bit lightweight!)
The Dan York Report audio podcast:
- (no podcast - too sick)
Monday, December 8
Deploy360 Programme:
Personal Sites:
The Dan York Report audio podcast:
Other:
- FIR podcast #785 – 12/8/14 - (includes my weekly report into FIR)
Tuesday, December 9
Deploy360 Programme:
Personal Sites:
- Disruptive Telephony: Catching Up With Mitel...
The Dan York Report audio podcast:
Wednesday, December 10
Deploy360 Programme:
Personal Sites:
- Disruptive Telephony: The Directory Problem – The Challenge For Wire, Talko And Every Other "Skype-Killer" OTT App (long post)
The Dan York Report audio podcast:
- (no podcast - too sick)
Thursday, December 11
Deploy360 Programme:
Personal Sites:
- Disruptive Conversations: Opinion - A New iPhone App Aiming To Make Podcasting Easy For Everyone
The Dan York Report audio podcast:
Friday, December 12
Deploy360 Programme:
- Congrats To Norway’s .NO On Over 5,000 DNSSEC-Signed Domains!
- Emily Taylor’s Must-Read Post: Ofcom in denial over UK IPv6 failure
Personal Sites:
- Monadnock Curling Club: Great Story About New Curling Club In Brooklyn, NY
The Dan York Report audio podcast:
- (no podcast)
Saturday, December 13
Deploy360 Programme:
- (no post)
Personal Sites:
The Dan York Report audio podcast:
Sunday, December 14
Deploy360 Programme:
- (no post)
Personal Sites:
- DanYork.com: Video: The Keene Interfaith Community Breakfasts
The Dan York Report audio podcast:
Now we'll see what the rest of the month brings...
An audio version of this post is available:
If you found this post interesting or useful, please consider either:
- following me on Twitter;
- adding me to a circle on Google+;
- following me on Ello;
- following me on App.net;
- subscribing to my email newsletter; or
- subscribing to the RSS feed.
Dec 15
TDYR 197 – Halfway Through December, How Is #Finish2014Strong Doing?
Dec 14
TDYR 196 – “Surprise Me, Santa”, A Fascinating Side Effect Of Raising A Child Without Commercial TV
Dec 14
Video: The Keene Interfaith Community Breakfasts
It's been quite an eye-opening experience for my wife and I, both in terms of learning about the quantity of people in our region who are homeless... but also in hearing some of the stories and knowing that while often it is very definitely choices that get people into these situations, sometimes it is instead circumstances - job losses, medical expenses, family issues - and that the line between those who have and those who have not can be very thin and fragile.
Recently a local community TV show recorded an episode with several of us who have been involved with the community breakfasts. I represented our church and spoke about some of the changes that being involved has brought about with me and our family.
Give it a listen... and if you are in the Keene, NH, area and interested in helping, we're always looking for people to help during these cold winter months!
What are the "community" breakfasts that take place at the Keene UU Church (KUUC) during the winter months? How did they get started? How are they an example of interfaith service programs? And how can people get more involved? In this episode 501 of her show "My Karma Ran Over My Dogma", Rev. Sandra Whippie explores these topics and much more with a panel including:
- Rev. Michael Hall, KUUC minister and member of the Interfaith Clergy Association
- Charlie Gibson, member of the Catholic churches in the Keene area
- Dan York, member of the Keene Unitarian Universalist Church (KUUC)
- Marcia Winters, member of the Keene United Church of Christ (UCC)
P.S. For the purpose of including an image for this post in the "carousel" at the top of the site, I'm including this screenshot of me talking:
Dec 13
Verizon Launches Voice Cypher Secure VoIP Mobile App… With A Government Backdoor
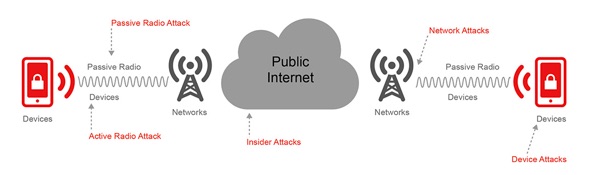
Verizon Wireless this week did something that initially seemed quite impressive – they launched “Voice Cypher”, an app available for iOS, Android and Blackberry that promises secure end-to-end encryption. It uses VoIP and is an “over-the-top” (OTT) app that works on any carrier. If you read the marketing material on their web site, it all sounds great! Indeed their “Learn More” page has all the right buzzwords and security lingo – and says quite clearly: Voice Cypher provides end-to-end encryption between callers, even if the call crosses over multiple networks.” They include the requisite network diagram that shows how it protects against all threats:
It turns out there’s just one small little detail … as reported by BloombergBusinessweek, the app comes complete with a backdoor so that Verizon could decrypt the phone calls if requested to do so by law enforcement!
As the Businessweek article states:
Cellcrypt and Verizon both say that law enforcement agencies will be able to access communications that take place over Voice Cypher, so long as they’re able to prove that there’s a legitimate law enforcement reason for doing so.
Unfortunately, in this post-Snowden era I don’t know that many of us put a great amount of trust in our governments to only access communications with a “legitimate law enforcement reason”. Or perhaps the concern is that what gets classified as “legitimate” can be widely construed to mean almost anything.
The article does point out that Verizon is bound by CALEA to provide lawful intercept to the phone networks, but points out an interesting caveat that Verizon could have used:
Phone carriers like Verizon are required by U.S. law to build networks that can be wiretapped. But the legislation known as the Communications Assistance for Law Enforcement Act requires phone carriers to decrypt communications for the government only if they have designed their technology to make it possible to do so. If Verizon and Cellcrypt had structured their encryption so that neither company had the information necessary to decrypt the calls, they would not have been breaking the law.
A Verizon Wireless representative indicated that they believe government agencies looking for ways to protect sensitive information may be customers of this service, as may be corporate customers concerned about leaking private information.
But… as we continue to hear more and more information about the massive amount of pervasive monitoring and surveillance by government agencies from many different governments around the world, you do have to wonder how safe those agencies and companies will feel with a “secure” solution that already comes with a backdoor. The problem with a known backdoor is that even if you may trust Verizon Wireless to only allow legitimate law enforcement access… how do you know that some attacker may not be able to penetrate that backdoor? The “secure end-to-end encryption” isn’t entirely secure.
Given that the service has a higher price tag of $45 per month per device, I do wonder how many businesses or agencies will actually embrace the service.
On reading about this Voice Cypher service, it certainly sounds quite interesting. We need more secure voice solutions out there – and it’s very cool that Verizon Wireless is delivering this as an OTT mobile app that will work across different carriers.
It’s just too bad that it’s not truly “secure end-to-end”. ![]()
P.S. I also recorded an audio commentary on this same topic.
Dec 13