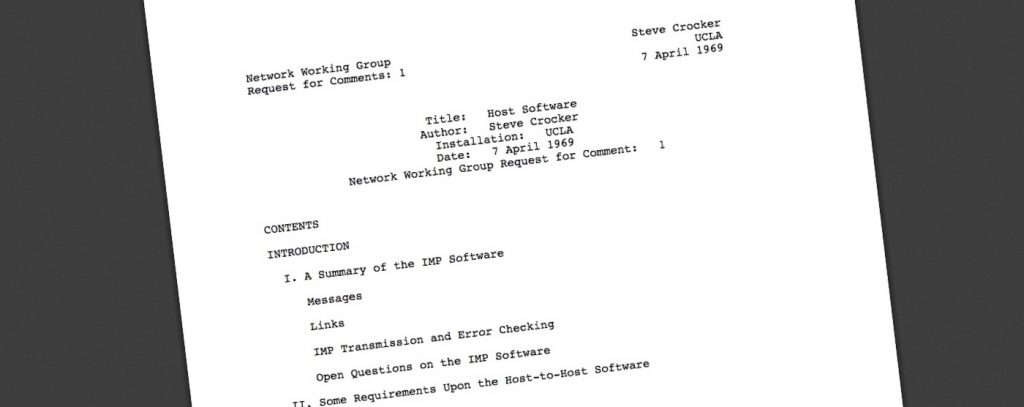
Hi! Remember this newsletter you subscribed to? The one you haven’t seen since back on April 22, 2024?
Welllllll… it’s been a wild ride… and an unplanned hiatus.
But… my goal now is to get back into this a bit more, and so I want to fire off this short note to just give a personal update.
Next time, I’ll be climbing up into that proverbial crow’s nest and looking out at the horizon ahead of us. For this newsletter… I’m going to look back instead at where the ship has sailed over the past few months.
If you visit my danyork.me aggregation site, you’d see that I have published some work articles… but nothing personal since the last issue (035) of this newsletter back on April 22, 2024. No blog posts. No podcast episodes. No newsletters. No livestreaming to Twitch. No… nothing. Zip. Nada. Zilch. Nichts.
So here’s the story…
The fun began back in early May when the 2017 iMac I’d been using to produce my podcasts, do all my livestreaming, and write many of my posts started acting really funky. It was acting very slow.. and freezing completely. Many reboots and upgrade attempts later, I was finally able to identify that it was having “S.M.A.R.T. disk errors”. Which wasn’t good.
“It’s dead, Jim” would be the Star Trek (Original Series) way to say it.
Given that it’s from 2017, I can’t upgrade it to the latest MacOS X. And heck, it’s so old Apple won’t even give me anything for a trade-in. (But they’ll help recycle it for me if I want.  ) Giving other things going on (see below!) fixing it has been super LOW priority… which has meant that my normal platform for content creation and production has been offline. So no podcast episodes or livestreaming.
) Giving other things going on (see below!) fixing it has been super LOW priority… which has meant that my normal platform for content creation and production has been offline. So no podcast episodes or livestreaming.
As that was all happening, a more massive disruption was entering our life – we adopted an 8-week-old puppy!
Named “Barkley”, he’s a very lovable and adorable mix of a pug and a miniature schnauzer (apparently called a “Schnug”) who keeps growing and growing and now at 6 months old is larger than our 17-year-old miniature poodle.
But.. my wife and I had never had a puppy before! We’ve had a couple of dogs (and cats) but they’ve all been a few years old when we adopted them. Anyone who has had a puppy probably understands what these last months have been like! Constantly watching where he is… “puppy-proofing” the entire house… constantly watching where he is… stopping him from eating everything… trying to train him a bit… constantly watching where he is… trying to prevent him from always attacking our 17yo dog… stopping him from eating whatever… oh, and constantly watching what he’s doing. It’s been… exhausting!
Basically like having a newborn child again… only one that can run fast all over and has sharp teeth! 
But in the end… he’s a wonderful addition and we’ve come to love him dearly. He’s curled up against my foot as I write this… and tomorrow night you’ll find me in a class with him.
While all of this was going on, I was also enrolled as a Climatebase Fellow in a very intense 12-week program of 10-15 hours of sessions each week all related to improving my understanding of the current state of information and science around climate change. As shown in the image below, it covered a very wide range of topics:

Participating in this fellowship was part of my professional development at my employer, the Internet Society. In the last issue, I pointed to my article about “The Internet and Climate Change” and that continues to be an area of great interest and exploration for me. I’ll undoubtedly write some future newsletters specifically around this whole area.
My interest was mostly to refresh my understanding of current climate thinking. I’ve been involved in “environmental” issues since the 1980s, and was very active in the broader movement in the early 1990s, serving in different volunteer leadership roles for different organizations. But then life took me away from that heavy involvement and my knowledge has aged. I heard phrases like “regenerative agriculture” but didn’t know what they meant. (Now I do!)
It was a good program and I met some great people and enjoyed participating in the community (which I am still doing).
As we came into summer here in Vermont, the Climatebase Fellowship wrapped up, but the intensity of the puppy and work and family and everything else continued.
And then a very cool opportunity was presented to me… at the Internet Society we had a new President and CEO, Sally Wentworth, start on September 1, 2024. Back in July she approached me about taking on a new role that we eventually called “CEO communications” where I’m helping with developing and executing plans across both the Internet Society and Internet Society Foundation for consistent communication from the CEO’s office internally, externally, and with our community and partners.
I formally took on this role on September 1 (and mentioned something on LinkedIn later) but began some aspects of it back in August. I’ve known Sally for the 13 years that I’ve been at the Internet Society (she’s been there 15 years) and have deep and great respect for her. So I’ve been excited about the new role, grateful for this opportunity to stretch my own skills in new and different ways… and just… busy! 
And now on this 24th day of September… it’s time to get back in the flow again and start creating some content again. There are so many stories to tell… so many changes happening… so much ahead on the horizon… both icebergs to avoid and opportunities to explore!
Time to climb up into that crow’s nest, whip out the spyglass, and get back to looking out ahead at the horizon and sharing what I see!
See you soon!
[The End]
Recent Posts and Podcasts
Here is some of the content I’ve published and produced recently on my personal sites:
- <nothing!>
[I do still contribute reports to the “monthly” episodes of the For Immediate Release podcast.]
I did publish some new posts for the Internet Society (who has no connection to this newsletter):
- Montana’s TikTok Ban: Breaking the Internet and Undermining Online Privacy
- Kenya Internet Disrupted Amidst Protests
- US Supreme Court Upholds Right of Websites to Moderate Content
- Global Tech Outage Demonstrates Need for Resiliency in Software Systems
- Texas’ Mandatory Age Verification Law Will Weaken Privacy and Security on the Internet
More on why so many of them are law-related… in a future newsletter!
Thanks for reading to the end. I welcome any comments and feedback you may have.
Please drop me a note in email – if you are a subscriber, you should just be able to reply back. And if you aren’t a subscriber, just hit this button  and you’ll get future messages.
and you’ll get future messages.
This IS also a WordPress hosted blog, so you can visit the main site and add a comment to this post, like we used to do back in glory days of blogging.
Or if you don’t want to do email, send me a message on one of the various social media services where I’ve posted this. (My preference continues to be Mastodon, but I do go on others from time to time.)
Until the next time,
Dan
Connect
The best place to connect with me these days is:
- Mastodon: danyork@mastodon.social
You can also find all the content I’m creating at:
If you use Mastodon or another Fediverse system, you should be able to follow this newsletter by searching for “@crowsnest.danyork.com“
You can also connect with me at these services, although I do not interact there quite as much (listed in decreasing order of usage):
- LinkedIn: https://www.linkedin.com/in/danyork/
- Soundcloud (podcast): https://soundcloud.com/danyork
- Instagram: https://www.instagram.com/danyork/
- Twitch: https://www.twitch.tv/danyork324
- TikTok: https://www.tiktok.com/@danyork324
- Threads: https://www.threads.net/@danyork
- BlueSky: @danyork.bsky.social
Disclaimer
Disclaimer: This newsletter is a personal project I’ve been doing since 2007, several years before I joined the Internet Society in 2011. While I may at times mention information or activities from the Internet Society, all viewpoints are my personal opinion and do not represent any formal positions or views of the Internet Society. This is just me, saying some of the things on my mind.