Just a guy in Vermont trying to connect all the dots...
Author's posts
Aug 24
Hashtag Support In Ello Helps Find Great Content
About three weeks ago, Ello added hashtag support and made it possible for people to find great content that is being posted on Ello. Paul Budnitz wrote about the launch (on Ello, of course) and included some examples (to which I've then added a few more):
- #art
- #design
- #architecture
- #music
- #typography
- #painting
- #gif
- #photography
- #technology
- #climatechange
- #politics
- #vermont
Obviously hashtags have been around on other social networks for quite some time. When Ello launched last year some people almost immediately asked where the hashtag support was.
Now it's here... and if you search on Ello (using simply https://ello.co/search ) you can now use hashtags as a great way to find new content - and to find new people to follow.
I'm still writing on Ello now and then - https://ello.co/danyork - partly out of just interest in trying a different service and partly because I like the _principles_ upon which Ello is founded. Now, hashtags are helping me find other people of interest who are posting new and different things.
If you're on Ello, or gave it a try back in the beginning and then haven't gone back, do check out the hashtag support and see what you may find...
Aug 23
Hobson & Holtz Report #822: The case against impressions as a digital metric
Intro: Red Folder is free for a year to those affected by fires in the U.S. West, IABC Fellows talk measurement and ROI live this Thursday on ‘Circle of Fellows’;
Quick News: Drones are taking off in the oil industry, the U.S. federal government partners with Yelp to get citizen reviews, personal photos at work: pictures that paint a thousand words; mobile messaging has come of age; CustomScoop promo;
News That Fits: The case against impressions as a digital metric; Dan York’s Tech Report: Terry Fallis’ latest novel, Comcast’s livestreaming app, the Auxy Beat Studio and Looopy (for layering looped recordings) for the iPad; listener comments; the past week on the FIR Podcast Network; Michael Netzley’s Asia Report: podcasting in India; Igloo Software promo; republishing older blog content: does it work?;
News about next week’s show; music from Jim Keller; and more.
Links to the content in this episode are on Delicious.
The post #822: The case against impressions as a digital metric appeared first on FIR Podcast Network.
Aug 19
Voice of VOIPSA in “Top 24 VoIP Blogs on the Internet”
It was nice to see this blog included in a recent “Top 24 VoIP Blogs on the Internet” post put out by Commander, who appears to be a provider of VoIP equipment, services and more:
http://blog.commander.com/top-24-voip-blogs-on-the-internet/
Obviously any list like this is very subjective but we do appreciate the mention, particularly given that the blogging here has slowed down dramatically. (And to that end, if anyone is interested in writing here about VoIP security, please contact me.)
Many of the other sites on that list are great ones to follow.
Aug 19
Video For All Those Parents Who Travel: "While I Was Away" by Pat Green
For all of those parents like me who travel a good bit, singer Pat Green recently put out this very well-done and quite touching video, "While I Was Away":
I'd honestly never heard of Pat Green before, but a work colleague shared the link on an internal forum. My work takes me away from my wife and kids for about 25% of the time ... so about 80-90 days a year... and it's definitely very hard on all of us. I'm thankful my job doesn't take me away more, as some of the other professions do. But each time I'm away, I do think of all the things they are learning and doing while I'm not there.
Beautiful song...
Aug 17
TDYR 261 – Working In Toronto For A Week
Aug 17
#821: The pitfalls of product promotion on social media
Intro: Next ‘Second Circle of IABC Fellows’ broadcast on August 27 with focus on measurement and ROI, we have a Patreon button on the FIR Podcast Network home page, the final episode of The Hobson and Holtz Report on September 7 won’t be face-to-face after all, Neville was interviewed by Joe Thornley on this week’s Inside PR 420 coming on Wednesday, FIR dinner in London with Kevin Anselmo on September 10;
Quick News: Press release services hacked, stolen releases used for insider trading; Blossombot, the New York Times’ Slack bot, helps decide which stories to post to social media; posting as Target customer service, man takes on haters of new gender-neutral policy; is Crowd Mics the answer to making events truly engaging?; CustomScoop promo;
News That Fits: The pitfalls of product promotion on social media: lessons to learn from Kim Kardashian’s drug-product promo on Instagram; listener comments; Igloo Software promo; Dan York’s Tech Report: Comcast to launch Watchable, Yahoo’s Livetext now available worldwide, no more 140-character limit on Twitter direct messages, Facebook should pay all of us says the New York Times, Ello hashtags; the past week on the FIR Podcast Network; Tinder’s Twitter meltdown: was it a planned PR stunt?;
Music from Adri-Anne Ralph; and more.
Links to the content in this episode are on Delicious.
The post #821: The pitfalls of product promotion on social media appeared first on FIR Podcast Network.
Aug 10
Hobson & Holtz #820: Marketing is shifting from agencies and moving in-house
Intro: The final episode of The Hobson and Holtz Report is coming in September, and more news about changes in FIR; new FIR Interview coming this week; two new FIR Podcast Network shows about to debut: YouTubular Conversations with Harry Hawk, EE Voice with Sharon McIntosh and Sharon Phillips;
Quick News: Is VR the future for Second Life?, the New York Times live-blogged GOP debate directly from Slack using a Chrome extension, 3 reasons Millennials are getting fired, beware the fake embedded tweet; CustomScoop promo;
News That Fits: Marketing is shifting from agencies and moving in-house; Dan York’s Tech Report, including Google’s handling of new top-level domains, a kerfuffle over Facebook videos, and WeChat and mobile in China; listener comments; controlling the media channels: can football win the game?; Igloo Software promo; the past week on the FIR Podcast Network;
Music from Ace & the Gulls; and more.
Links to the content in this episode are on Delicious.
The post #820: Marketing is shifting from agencies and moving in-house appeared first on FIR Podcast Network.
Jul 31
Firechat Enables Private Off-The-Internet (P2P) Messaging Using Mobile Phones
There was a fascinating article posted on Medium this week by the CTO of messaging app Firechat:
In the text he outlines how they do decentralized "off-the-grid" private messaging using an ad hoc mesh network established between users of the Firechat app. It sounds like the app instances join together into some kind of peer-to-peer (P2P) network and then do normal "store-and-forward" messaging.
Of note, the apps do NOT need an Internet connection, or even a cellular network connection - instead they can use the Bluetooth and WiFi radios in the mobile phones to create a private mesh network and connect to other users of the Firechat app.
Naturally, having spent some time exploring P2P networks back when I was playing around with P2P SIP and distributed hash tables (DHTs) and other technologies, I immediately jump into the techie questions:
- How are they routing messages from one user to another?
- How is the "directory" of users in P2P mesh maintained?
- What addresses are they using for the communication? Is this still happening over IP addresses? Or are they using some other kind of addressing?
- How do users join and leave the mesh network?
- How do user get authorized to join the private mesh? (Or is it just open to all?)
- How secure is the communication between the parties?
- Is the message encrypted or private in any way? Or is it just plain text?
- How well do smartphone batteries hold up if multiple radios are being used? What is the power impact of joining into a mesh network like this?
None of that is covered in this article, of course... this piece is more about the theory of how this can work given a particular density of users. It introduces the phrase "percolation threshold" and provides some background and research into how these kind of networks can be created.
I've always been fascinated by P2P networks like this sounds to be. The beauty of the Internet... the "Internet Way", so to speak... has been to support distributed and decentralized architectures.
If you think about mail or web servers, they are (or at least were) massively distributed. Anyone could set up a mail or web server - and millions upon millions of them bloomed. While we've certainly seen a great amount of centralization due to market dominance (ex. Gmail), the architecture still is distributed / decentralized.
Except... of course, the directory is still centralized. Mail and web servers rely on the central directory of DNS to resolve domain names into IP addresses so that connections can occur. Most other applications rely on DNS for this as well.
Hence my curiousity about how Firechat is handling the directory and routing issues.
I'm also intrigued by how the article hints at integrating Internet-connected users into the P2P mesh. So you really have a hybrid network that is part P2P and part connected out to cloud-based servers.
(And all of this brings me back to those early days of Skype 8-10 years ago when so many of us were captivated by the P2P mechanisms they created... most all of which is now gone in the post-Microsoft-acquisition as Skype has moved from P2P to server/cloud-based - with one big reason being given that mobile devices apparently had speed and battery life issues participating in true P2P networks.)
A key challenge Firechat faces, of course, is the "directory dilemma" of building up the quantity of users where P2P mesh networks like this can happen. This is the same dilemma facing basically all over-the-top (OTT) messaging apps. "Percolation theory" requires a certain user density for a mesh like this to work.
That will be their struggle.
And in some urban areas I can see this working quite well. Perhaps not so much out in the woods of New Hampshire where I live!
But I wish them well with this. I love to see new explorations of potential new architectures for communication. And I can certainly see instances when ad hoc, distributed/decentralized P2P meshes like these could be quite useful.
And I'm definitely looking forward to some more technical articles that dive down into some of these questions.... I do hope they'll write more soon!
Photo credit: Stanislav Shalunov's article about Firechat
Jul 31
Firewalls Now Looking At Intercepting SSH Traffic Via A MITM Attack
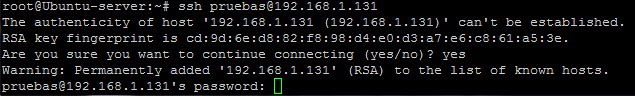
Can you trust Secure Shell (SSH) when you are behind certain firewalls? That’s the question raised by a post from a friend of mine:
It seems that because ssh can be used for tunneling services and application traffic several firewall vendors are now implementing “SSH inspection” services that essentially perform a Man-in-The-Middle (MITM) attack on your ssh connection.
When you go to ssh into a server, the firewall pretends it is that server and creates a ssh tunnel with you. The firewall then creates the actual ssh connection to the server and passes your packets from the first tunnel into the second tunnel – while being able to log or inspect the packets in between the two tunnels.
Now, of course with ssh you go through an initial handshake when you first connect to a server that results in the server’s public key being added to your list of known hosts.
If you connect to a server for the first time BEFORE being behind one of these firewalls doing SSH inspection, you would already have the correct public key of the server in your known hosts file. What would happen when the firewall tried to do a MITM is that you would be asked to approve the public key of the server again. (Because you are actually now approving the public key of the firewall.)
You would have to realize that this was wrong and stop your connection!
If you proceeded ahead with the connection and approving the public key, you would now have the firewall as a MITM.
If you connect to a server for the first time AFTER being behind one of these firewalls, well… I’m not sure what you can do. You’re going to see a public key to approve, but it would be from the firewall! You’d have to somehow learn the correct public key of the target server to be able to match it to the fingerprint you are being shown.
I don’t know how well that will work.
The good news for me personally is that I’m not behind these kind of firewalls in my regular networks – although I don’t honestly know what my Internet service providers are using. They could be doing these kind of things.
I don’t consider this a good thing that firewalls are now doing this. We need to trust the security of services like SSH. This decreases overall trust.
Photo credit: El Taller del Bit on Flickr