Just a guy in Vermont trying to connect all the dots...
Author's posts
May 27
China Passes 900 Million Cell Phone Users! (Featured Blog)
May 25
Skype Issues Official Statement About the End of Skype for Asterisk (Featured Blog)
May 24
FBI’s Newest VoIP Fraud Case Shows Danger of Social Engineering
As I note in that blog post, this wasn't a "VoIP security" attack as much as it was a social engineering attack. This group went to rather remarkable lengths to convince ITSPs that they were legitimate businesses to whom the ITSPs should extend credit... and then they abused that credit once it was given.
In the book, I talk about these issues of both fraud and social engineering. From a protection point-of-view, this latest fraud case really highlights the uncertainties in the "SIP Trunking" space (a topic I focused on in Chapter 5) and the need to perform adequate due diligence on the ITSPs from whom you are purchasing SIP connectivity. (Although, admittedly, this particular group went to such lengths that it is not surprised they duped do many companies.)
The reality is that as the market for Unified Communications and IP communications continues to grow and expand, it will only become more tempting for scammers and thieves... so I expect we'll see even more fraud cases in the time ahead.
May 20
My Github repo of SMSified experiments
 Earlier in the week I mentioned a quick python app I wrote to send SMS messages using SMSified. I’m storing that code and some other experiments up in a Github repo at:
Earlier in the week I mentioned a quick python app I wrote to send SMS messages using SMSified. I’m storing that code and some other experiments up in a Github repo at:
If you are a Github user and also interested in building SMS apps, please feel free to “watch” that repo and follow along with my own experiments. Code will probably be a mixture of python and Node.js, with occasional other languages thrown in.
May 19
Skulpt – a JavaScript-based way to run Python inside your web browser
 In the process of writing about the site that lets you run Linux in your web browser, I learned about Skulpt.org that is essentially the same idea only for a python command line.
In the process of writing about the site that lets you run Linux in your web browser, I learned about Skulpt.org that is essentially the same idea only for a python command line.
The demo at www.skulpt.org is pretty cool… just modify the python code in the screen and press Ctrl+Enter to execute the code and have the output appear in the box below.
To play with it yourself, you can get the code at http://code.google.com/p/skulpt/ or as author Scott Graham shows on the Skulpt.org page you can just use mercurial to clone the repo.
I haven’t installed it myself… again, like the “Linux in your browser” experiment, I think this is very cool but I’m not entirely sure where I’d personally ever use. Still, I’m very glad people build projects like this – if for no other reason than showing that this could be done!
Cool stuff…
May 18
Greg Bayer: How to Move Files From One Git Repo To Another While Preserving History
By way of a Hacker News post, I learned of this great post by Greg Bayer:
Moving Files from one Git Repository to Another, Preserving History
I’ve actually had a couple of cases where I’ve wanted to move some files and keep the history. I couldn’t easily figure it out and opted to just copy the files into the new repo and lose the history. This looks like a workable solution instead. Thanks to Greg Bayer for writing it up.
P.S. a comment to the HN post also mentions this “git-subtree” tool, which does look interesting.
May 17
A Quick Python App to Send SMS via SMSified’s REST API
 Today Voxeo[1] launched SMSified a new service that lets you use a really simple RESTful API to send text messages within the US for only 1 cent per message. I and other colleagues have been writing about SMSified on the SMSified blog and after writing a tutorial about using SMSified with curl, I figured I’d play around with python a bit and code up an example of sending a SMS via python.
Today Voxeo[1] launched SMSified a new service that lets you use a really simple RESTful API to send text messages within the US for only 1 cent per message. I and other colleagues have been writing about SMSified on the SMSified blog and after writing a tutorial about using SMSified with curl, I figured I’d play around with python a bit and code up an example of sending a SMS via python.
So here it is… stored up in my Github account, but also here:
[python]
#!/usr/bin/env python
# Really simple python app for playing with sending SMS messages
# via SMSified – http://www.smsified.com/
# Created by Dan York – May 2011
import json
import urllib
senderid = "dandemo" #SMSified account
password = "notmyrealpassword" #SMSified password
sendernum = "5853260800" #SMSified phone number
apiurl = "https://"+senderid+":"+password+"@api.smsified.com/v1/
smsmessaging/outbound/"+sendernum+"/requests"
address = "14079678424" # Phone num to which you want to send
message = "Hello there" # Whatever msg you want to send
data = urllib.urlencode(((‘address’,address),(‘message’,message)))
f = urllib.urlopen(apiurl,data)
print json.loads(f.read())[‘resourceReference’][‘resourceURL’]
[/python]
As you can see in the code, there are really only three lines of importance: the one building “apiurl”; the one urlencoding the data; and the one opening the URL. The rest are really just for the convenience of using variables.
The final line simply prints out the info included in the result JSON. I was going to (and still may) make that print out prettier or say something more… and if you are reading this sometime in the future, the version on Github may have already morphed and evolved into something different. The point is that now that you get JSON back, you can parse it and start to take action on it.
Anyway, this was just a quick sample app to experiment with SMSified. If you have checked out the new service, it’s free to set up a developer account and currently is free entirely during the beta period.
[1] In full disclosure, Voxeo is my employer.
May 17
Fun Tool to Run a Linux Computer IN Your Browser Using JavaScript
Here’s a fun little JavaScript experiment… go to:
Watch the boot sequence… and… ta da… you’ve got a Linux root prompt! Use basic Linux commands, edit files with vi, compile apps in C using “tcc”.
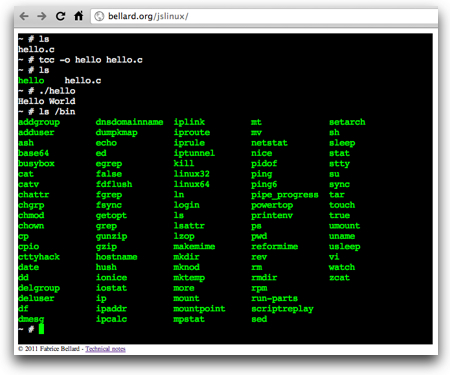
Fabrice Bellard explains why he wrote this JavaScript PC emulator.
My immediate thought was how this could be used for teaching people Linux. Regardless of what it is used for or whether it’s just a fun experiment, it’s very cool to see that JavaScript engines in the latest browsers can support this type of more complex activity. Kudos to Fabrice Bellard for writing this!
Also check out:
- Hacker News discussion about this tool
- Fabrice Bellard’s home page showing his other tools
- Article about him: “Fabrice Bellard: Portrait of a Superproductive Programmer”
May 10
The End of the “Skype as Bandit” Era (Featured Blog)
Apr 24
Deep Tech Dives Into Cloud Availability In Light Of Amazon’s EC2/EBS Problems From Joyent and enStratus
With Amazon’s ongoing struggles with part of their cloud, I’ve obviously been watching closely, given that I work for a company that provides a cloud for communication applications (hosted almost entirely on our own global carrier-grade infrastructure). Watching Amazon’s status site, they continue to not be entirely back in action a couple of days later.
There have been a lot of great technical posts out there related to what’s happening with AWS. Two that caught my eye are admittedly by an Amazon competitor, Joyent, but are definitely worth a read:
- On Cascading Failures and Amazon’s Elastic Block Store
- Magical Block Store: When Abstractions Fail Us
The latter post about abstraction layers hits a few major points with me, particularly around the need for abstraction layers to allow some type of control… and some type of transparency into what is going on.
Black boxes are great… until they break.
Another great post was by George Reese over in the O’Reilly Community (he is CTO of enStratus, a company making equipment to assist in infrastructure automation):
Reese argues that it is the application developer’s responsibility to design apps in such a way that they aren’t dependent at all on the underlying infrastructure.
This all takes me back to my post I wrote in 2009 about the need for services to be distributed and decentralized. Now I was talking in there about Twitter and Facebook… but the same argument can be made for apps in general…
It’s a fascinating time… I hope for Amazon’s sake that they can get everything back in action soon… and it will be interesting to see what questions this all makes developers ask with regard to cloud providers. Meanwhile, I’m enjoying many of these deep technical posts… I expect to see more coming in the days and weeks ahead.

