Just a guy in Vermont trying to connect all the dots...
Author's posts
Feb 05
TDYR #091 – Oh, How The English Language Evolves – 3 Words That Amused Me Today
Feb 05
Comcast’s Speedtest Now Breaks Out IPv6 Speed Vs IPv4 Speed
A tip from John Jason Brzowski let us know that Comcast’s Internet speed test at speedtest.comcast.net now performs speed tests over both IPv6 and IPv4 and shows you the results separately. This is a public test that anyone can use, regardless of whether you are a Comcast customer or not. Perhaps obviously, for the IPv6 test to work you need to either have native IPv6 connectivity from your ISP or you need to have an IPv6 tunnel for your network. Without that you’ll just get a regular old IPv4 test.
Naturally I had to try this out and was quite pleased with the results. I am NOT a Comcast customer so the results are for another ISP. I do have native IPv6 connectivity so this was not tunneled traffic. Here was my test yesterday with the closest geographic server (which may or may not relate to network proximity – I didn’t do much checking on that):
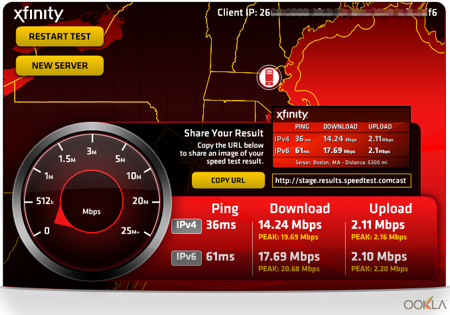
Of course I was pleased that IPv6 was faster! I assume this probably had to do with more congestion on the IPv4 network at the precise time I did the test. As you’ll see below, IPv6 was not always faster.
For those familiar with these type of speed tests, the test performed two separate upload and download cycles for IPv4 and IPv6. As you can see from the center of the image a cool feature is that you can get a link to an image that you can then share out to social networks or use in other places. For example, here is the link to my image:
 Now, of course I had to try this multiple times during yesterday to see how the results varied – and as is true with pretty much all of these speedtest sites the results DID vary widely. Some of the results included:
Now, of course I had to try this multiple times during yesterday to see how the results varied – and as is true with pretty much all of these speedtest sites the results DID vary widely. Some of the results included:


I tried other servers in other parts of the US and had similar types of variation.
And then to my amusement I tried the test today shortly before writing this post and found that my speed has degraded significantly. Two results from Boston and one from the New Jersey server:



Just to check I tried a couple of other speed test sites and they provided similar results today. Now the explanation for this drop in my own bandwidth is probably pretty simple.
Snow.
Today we’re experiencing a major snowstorm here in New Hampshire (and all of the northeast USA) and so all the schools are closed and many kids are at home along with parents who need to be home with them. So people are undoubtedly streaming more movies, playing more online games and just consuming much more online bandwidth than they usually do during the day. My Internet connection is through my local cable provider… so it’s shared through my neighborhood, and so there we are. Tomorrow when everyone goes back to school my daytime speed should increase! 🙂
All comments about snow aside, this is very cool for Comcast to break out the speeds by protocol this way. They are of course NOT the only speed test out there that does this. Other IPv6 vs IPv4 speed tests include sites such as http://ipv6-test.com/speedtest/ and http://www.speedtest6.com/
Congrats to the team at Comcast for making this available!
P.S. I’d note that Comcast has to be collecting some fascinating measurements out of this effort because they are gathering test results from not only their own customers but also from all of their competitor’s customers who use this test site. They can then come up with statistics and metrics about the performance of those competitor networks. A rather brilliant move by someone within Comcast! Now… what would be great for the larger Internet community would be if they could also find some way to perhaps expose some aggregated level of information about what they are are seeing in terms of IPv6 performance across the range of ISPs from people using the site… maybe a topic for a presentation by someone at Comcast at a future event? (Hint, hint…)
The post Comcast’s Speedtest Now Breaks Out IPv6 Speed Vs IPv4 Speed appeared first on Internet Society.
Feb 05
Comcast’s Speedtest Now Breaks Out IPv6 Speed Vs IPv4 Speed
A tip from John Jason Brzowski let us know that Comcast’s Internet speed test at speedtest.comcast.net now performs speed tests over both IPv6 and IPv4 and shows you the results separately. This is a public test that anyone can use, regardless of whether you are a Comcast customer or not. Perhaps obviously, for the IPv6 test to work you need to either have native IPv6 connectivity from your ISP or you need to have an IPv6 tunnel for your network. Without that you’ll just get a regular old IPv4 test.
Naturally I had to try this out and was quite pleased with the results. I am NOT a Comcast customer so the results are for another ISP. I do have native IPv6 connectivity so this was not tunneled traffic. Here was my test yesterday with the closest geographic server (which may or may not relate to network proximity – I didn’t do much checking on that):
Of course I was pleased that IPv6 was faster! I assume this probably had to do with more congestion on the IPv4 network at the precise time I did the test. As you’ll see below, IPv6 was not always faster.
For those familiar with these type of speed tests, the test performed two separate upload and download cycles for IPv4 and IPv6. As you can see from the center of the image a cool feature is that you can get a link to an image that you can then share out to social networks or use in other places. For example, here is the link to my image:
 Now, of course I had to try this multiple times during yesterday to see how the results varied – and as is true with pretty much all of these speedtest sites the results DID vary widely. Some of the results included:
Now, of course I had to try this multiple times during yesterday to see how the results varied – and as is true with pretty much all of these speedtest sites the results DID vary widely. Some of the results included:


I tried other servers in other parts of the US and had similar types of variation.
And then to my amusement I tried the test today shortly before writing this post and found that my speed has degraded significantly. Two results from Boston and one from the New Jersey server:



Just to check I tried a couple of other speed test sites and they provided similar results today. Now the explanation for this drop in my own bandwidth is probably pretty simple.
Snow.
Today we’re experiencing a major snowstorm here in New Hampshire (and all of the northeast USA) and so all the schools are closed and many kids are at home along with parents who need to be home with them. So people are undoubtedly streaming more movies, playing more online games and just consuming much more online bandwidth than they usually do during the day. My Internet connection is through my local cable provider… so it’s shared through my neighborhood, and so there we are. Tomorrow when everyone goes back to school my daytime speed should increase! ![]()
All comments about snow aside, this is very cool for Comcast to break out the speeds by protocol this way. They are of course NOT the only speed test out there that does this. Other IPv6 vs IPv4 speed tests include sites such as http://ipv6-test.com/speedtest/ and http://www.speedtest6.com/
Congrats to the team at Comcast for making this available!
P.S. I’d note that Comcast has to be collecting some fascinating measurements out of this effort because they are gathering test results from not only their own customers but also from all of their competitor’s customers who use this test site. They can then come up with statistics and metrics about the performance of those competitor networks. A rather brilliant move by someone within Comcast! Now… what would be great for the larger Internet community would be if they could also find some way to perhaps expose some aggregated level of information about what they are are seeing in terms of IPv6 performance across the range of ISPs from people using the site… maybe a topic for a presentation by someone at Comcast at a future event? (Hint, hint…)
Feb 04
TDYR #090 – The Calm Before The (Winter) Storm
Feb 04
NLnet Labs Releases Helpful DNSSEC Infrastructure Audit Framework
 How secure is your DNSSEC infrastructure? If you operate a registry for a top-level domain (TLD) or if you are a DNS operator providing DNSSEC signing services, how secure are your operations? And how secure are your mechanisms for communicating DNSSEC information with registrars and other entities? Or, if you are a security auditor or researcher, how can you best assess the security of your client’s DNSSEC infrastructure?
How secure is your DNSSEC infrastructure? If you operate a registry for a top-level domain (TLD) or if you are a DNS operator providing DNSSEC signing services, how secure are your operations? And how secure are your mechanisms for communicating DNSSEC information with registrars and other entities? Or, if you are a security auditor or researcher, how can you best assess the security of your client’s DNSSEC infrastructure?
To help assess DNSSEC infrastructure and answer questions like these, the great folks at NLnet Labs recently released a “DNSSEC Infrastructure Audit Framework” available publicly for anyone to use. You can download the document and use it as a checklist to audit your own infrastructure or that of someone else.
As noted in the introduction, this document is not intended to be any kind of formal standard or assessment, but rather a guide and checklist to help people looking to understand how secure their DNSSEC infrastructure is:
A DNSSEC audit is the process of structural examination of a DNSSEC infrastructure. The purpose of this process is to evaluate the level of assurance of the system. This is achieved by reviewing the implementation and operation of the system controls and whether they are in compliance with the corresponding policy requirements or, in absence of formal policies, with best current industry practices.
A key document for performing an audit is a review checklist. The review checklist provides structure of the actual work and gives confidence that the audit scope is adequately covered. This document is a generic checklist for a DNSSEC review and provides a framework that assists auditors to perform an actual DNSSEC audit. However, the actions herein do not conform any formal audit standards and are merely intended to provide directions of how an audit might look like.
This document is neither standard nor best practice and is not suitable for any form of formal certification. Its intention is to offer a basis for a structured review of a DNSSEC environment.
The authors welcome feedback on this document so that it can mature. The licensing terms of the document are such that any entity may modify and publish the document on their own terms as long as NLnet Labs is being acknowledged. Incorporation in other documents, including standards is encouraged.
This is great contribution to the larger work of DNSSEC deployment and we thank Matthijs Mekking and Olaf Kolkman for both writing this document and then also making it public under a lenient license.
We hope many of you will find it helpful and do encourage you to provide feedback to Matthijs and Olaf. Using documents like this we can make the Internet more secure!
Feb 03
TDYR #089 – The Venomous Reactions To Coke’s SuperBowl Ad Show We Still Have Much Work To Do
Feb 03
CircleID: Thinking Strategically About the Benefits of IPv6
 I love it when my Monday morning begins by seeing posts like this one: Thinking Strategically About The Benefits of IPv6 by Mukom Akong Tamon. Please go over there and read that piece. He’s absolutely right that we need to be thinking about IPv6 beyond simply the fact that IPv4 addresses are on their way to being exhausted. I love his conclusion (my emphasis added):
I love it when my Monday morning begins by seeing posts like this one: Thinking Strategically About The Benefits of IPv6 by Mukom Akong Tamon. Please go over there and read that piece. He’s absolutely right that we need to be thinking about IPv6 beyond simply the fact that IPv4 addresses are on their way to being exhausted. I love his conclusion (my emphasis added):
One of these types of organisation will lead the provision of devices, software and services for tomorrow’s Internet, the other type will lose relevance and then will play catch up. Just remember this: The day you see concrete data to show the benefits of IPv6, it means you are already late to the game, that data will be coming from an early mover who is already making a ‘killing’ with IPv6.
Also, check out this great comment on the post (over on Mukom Tamon’s own site) that begins with:
It is in fact, the mobile arena that will deploy IPv6, we as a small company have already migrated to IPv6 and see huge benefits…
Great to see people relaying that they are already seeing the benefits of making the move to IPv6! (And yes, I think I may try to contact them to find out more about their situation.)
What are you waiting for? Are you going to be a leader in your field and seize any opportunities that are made possible with IPv6? Or are you going to wait until the last possible moment?
Feb 03
FIR #741 – 2/3/14 – For Immediate Release
Feb 02
TDYR #088 – Kudos To The NFL And Fox Sports For Streaming The Super Bowl Live To Cord-cutters
Feb 02
Slides: Case Study Of An IPv6 Addressing Plan (RIPE67)
How do you best plan how to allocate IPv6 addresses across your network? In addition to the resources we already link to on our IPv6 Address Planning page, this case study presented back at RIPE 67 in October also provided a nice graphical illustration of one way in which you could allocate IPv6 addresses:
The answer of course comes down to “it depends” upon the configuration and situation of your specific network environment. Cases studies like this one, though, help provide yet another view of how you can set up IPv6 on your network.
What about you? What is stopping you from deploying IPv6 today?



