Just a guy in Vermont trying to connect all the dots...
Author's posts
Jul 28
Code.DanYork.Com Now Back Available Over IPv6
 After a Reddit thread started up that briefly referenced a 2011 post I wrote about adding IPv6 to Node.js apps, I was contacted by a Redditor who was surprised that my site wasn’t available over IPv6!
After a Reddit thread started up that briefly referenced a 2011 post I wrote about adding IPv6 to Node.js apps, I was contacted by a Redditor who was surprised that my site wasn’t available over IPv6!
HUH???
I was surprised, too, because this site is hosted on a dual-stack server at Hurricane Electric and has been accessible over IPv6 since June 7, 2011, right before the World IPv6 Day event.
But in checking into it… there was no AAAA record in DNS for “code.danyork.com” that would point to the server, so the report was indeed accurate. For regular users this site was not available over IPv6.
It turned out to be one of those system administration issues that can bite you. A month or two ago, TypePad, the provider I still use for my personal DanYork.com site, experienced a severe DDoS attack that took many sites offline. They recovered but in doing so changed the way that sites were referenced a bit. I had to switch to using a CNAME instead of an IP address as I had been doing. The problem there is that due to the “no CNAME at zone apex” rule of DNS, I could no longer use just “http://danyork.com” – I would have to switch to using “http://www.danyork.com/”.
The episode highlighted to me, though, the need to be sure I have “Test over IPv6” in my list of things to check after making any major changes to any of my sites!
I didn’t want to switch and so I moved the DNS for “danyork.com” over to CloudFlare to make use of their “CNAME Flattening” so that I could still use “danyork.com”.
However, in moving the DNS info from my previous DNS hosting provider to CloudFlare, I messed up. I didn’t bring across the AAAA record for code.danyork.com. Also, very bizarrely, I didn’t have the “Automatic IPv6” setting enabled for danyork.com – even though it is now supposed to be on by default for all new domains.
So the fix was simple – I added the AAAA record for code.danyork.com, and I also flipped the switch on the Automatic IPv6 gateway. Now both code.danyork.com and danyork.com are fully available over IPv6.
Jul 28
FIR #766 – 7/28/14 – For Immediate Release
Jul 27
TDYR #167 – The Livestreaming Nightmare – What Do You Do When The Service Goes Down?
Jul 25
TDYR #166 – Recording on a Noisy Turboprop Plane
Jul 25
Techquickie Video: IPv4 vs IPv6 as Fast As Possible
It’s Friday… so it’s a good time to point out a “Techquickie” video from Linus Sebastian on the topic of “Internet Protocol - IPv4 vs IPv6 as Fast As Possible“. Yes, I have a few minor technical nits with the video (such as the impossible IPv4 addresses) and I’m not entirely in agreement that ISPs are the major issue (although they certainly are a part of the issue), but hey, it’s a fun introduction to IPv6 and the issues of IPv4 address exhaustion. I had not see any videos from Linus Sebastian before but I enjoy his energy and enthusiasm. ![]()
The good news is that a video like this gets discussion of IPv6 out to what seems to be a good-sized audience that he has developed through this various YouTube channels. Similarly I can see from the Reddit discussion that the video has already stirred up some good discussions. That’s all good!
And to that point… if you want to figure out what you need to do to get started with IPv6, check out our START HERE page to find resources aimed at your type of organization – and please let us know if you can’t find the resources that will help you!
Jul 25
Deploy360@IETF90, Day 5: HOMENET, SIDR, TRANS and GROW… and then we’re done!
 You might think the final day of IETF 90 might be a bit quieter for us… but in fact the morning session from 9:00-11:30 EDT has three sessions happening simultaneously that are related to the work we do (HOMENET, SIDR and TRANS) – and in my personal case I want to be in two separate places at the same time! (Which I will be attempting to do via monitoring Jabber chat rooms.) The day will actually start at 8:00am with an informal breakfast meeting of some of the folks subscribe to the DNSSEC coordination mailing list. After that we’ll be heading into the morning session block where we’ll be choosing between the three conflicting sessions.
You might think the final day of IETF 90 might be a bit quieter for us… but in fact the morning session from 9:00-11:30 EDT has three sessions happening simultaneously that are related to the work we do (HOMENET, SIDR and TRANS) – and in my personal case I want to be in two separate places at the same time! (Which I will be attempting to do via monitoring Jabber chat rooms.) The day will actually start at 8:00am with an informal breakfast meeting of some of the folks subscribe to the DNSSEC coordination mailing list. After that we’ll be heading into the morning session block where we’ll be choosing between the three conflicting sessions.
One of those three sessions is HOMENET, which Chris described in his Rough Guide post about IPv6:
(HOMENET) is chartered to address the challenges in the evolving networking technology within and among relatively small “residential home” networks. This work is not necessarily dependent on a specific version of IP but the thrust of all discussions within the WG is how the IPv6 protocol suite can better serve these often overlooked networks out at the consumer edge of the Internet.
The HOMENET agenda is filled with IPv6-related drafts and discussion points… BUT… there is also a DNSSEC angle that I described in my own Rough Guide post:
the HOMENET Working Group has on its agenda two documents from Daniel Migault that that look at two different aspects of DNSSEC interaction with customer-premise equipment (CPE). The first draft outlines an architecture in which a CPE device could manage some of its naming services and then outsource other naming services, such as DNSSEC management, to external services. The second draft proposes new DHCP optionsthat would provide a means to update the trust anchors used in DNSSEC and also provide a way to update the time of a CPE device. These are both definitely important work as we need CPE devices to provide solid DNSSEC support if we are to get DNSSEC validation happening everywhere.
The challenge for me is that one floor down in the hotel the TRANS working group will also be talking about DNSSEC. As I said in the Rough Guide post:
the TRANS Working Group focused on “Certificate Transparency” (CT) will be having a discussion about whether there is a role for CT to play in logging DNSSEC information. There is not a draft associated with this idea but there was a lengthy discussion in the trans mailing list that began with a message from Nico Williams and continued on into great detail. My understanding is that the discussion will be mainly about what, if any, role CT might play with DNSSEC and DANE. Given some of the passions involved with this whole topic I expect there to be a great amount of discussion.
Meanwhile, in a room nearby to TRANS, the Secure Inter-Domain Routing (SIDR) working group that focuses on securing BGP will be meeting. As our colleague Andrei Robachevsky wrote in his Rough Guide post about routing resiliency, there is a great amount of work happening in this group this week. Of particular interest may be a discussion around “RPKI Revisited” led by Geoff Huston about the Resource Public Key Infrastructure (RPKI). As Andrei writes:
Perhaps a bigger change that is being discussed is related to the problem of potential operational fragility in the management of certificates in the RPKI in response to the movement of resources across registries described by the draft “RPKI Validation Reconsidered”. The problem in a nutshell is that in the current model, specified by RFC 6487, a certificate is considered invalid if a proper validation path cannot be built for all resources specified by that certificate. But in operational reality such a situation can occur, for instance, with the resource transfer, when “shrinkage” of the parent certificate will immediately invalidate the whole branch beneath, unless all subordinate certificates are also re-issued. If such a situation happens high in the hierarchy, say at the RIR level, the impact can be pretty severe. The draft also describes alternative approaches, although the focus of the discussion now is on the problem.
After those three sessions in the first meeting block, the second meeting block really has for us only the Global Routing Operations (GROW) Working Group. The GROW agenda covers a number of routing security topics, one of which, as Andrei writes, deals with the issue of route leaks:
One of the items, which originally emerged in the SIDR WG and has now also been discussed in the GROW WG, is so-called “route-leaks”. Simply speaking, this describes a violation of a “valley-free” routing when, for example, a multi-homed customer “leaks” an announcement from one upstream provider to another one. Since usually customer announcements have the highest priority, if no precautions are taken this results in traffic from one provider to another bypassing the customer. This introduces the potential for a staged MITM attack. But this is an explanation in layman terms, and the group was working on nailing down the definition and the problem statement, see https://datatracker.ietf.org/doc/draft-ietf-grow-simple-leak-attack-bgpsec-no-help/.
After that, our team will be attending the regular meeting of the Internet Society Advisory Council and then will be starting the process of heading home! As you can tell from our posts, it’s been a VERY busy – but successful – week!
If you’d like to join the HOMENET, SIDR or GROW sessions (or any of the others) remotely to hear the discussion you can follow the instructions on the IETF 90 Remote Participation page or use the “tools-style” agenda page that provides easy links to the audio stream, jabber chat room documents and more for each of the sessions.
The information about the relevant working groups today is:
HOMENET (Home Networking) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/homenet/
Documents: https://datatracker.ietf.org/wg/homenet/
Charter: https://datatracker.ietf.org/wg/homenet/charter/
(Friday, July 25, 2014, 0900-1130 EDT, Canadian)
TRANS (Public Notary Transparency) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/trans/
Documents: https://datatracker.ietf.org/wg/trans/
Charter: https://datatracker.ietf.org/wg/trans/charter/
(Friday, July 25, 2014, 0900-1130 EDT, Manitoba)
SIDR (Secure Inter-Domain Routing) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/sidr/
Charter: https://datatracker.ietf.org/wg/sidr/charter/
(Friday, 25 July, 0900-1130 EDT, Territories Room)
GROW (Global Routing Operations) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/grow/
Charter: https://datatracker.ietf.org/wg/grow/charter/
(Friday, 25 July, 1150-1320 EDT, Ontario Room)
For more background on what is happening at IETF 90, please see our “Rough Guide to IETF 90″ posts on the ITM blog:
- Rough Guide to IETF 90: DNSSEC, DANE and DNS Security (see also our Deploy360 post on the topic)
- Rough Guide To IETF 90: IPv6 Is Everywhere, eh?
- ISOC Rough Guide to IETF 90: Routing Resilience
- Overview: ISOC Rough Guide to IETF 90: Toronto, Eh?
If you are here at IETF 90 in Toronto, please do feel free to say hello to a member of the Deploy360 team. And if you want to get started with IPv6, DNSSEC or one of our other topics, please visit our “Start Here” page to find resources appropriate to your type of organization.
Jul 24
Deploy360@IETF90, Day 4: 6LO, DNSSD, SUNSET4 and Learning About 5G Wireless Technology…
 Today at IETF 90 we on the Deploy360 team will be starting the day focusing on the “Internet of Things (IoT)” as we listen to what is being discussed in the 6LO working group. Formally titled “IPv6 over Networks of Resource Constrained Nodes” this group focuses on using IPv6 in low power and constrained environments such as sensor networks, “smart grids” and other embedded environments. The 6lo agenda is full of drafts exploring different types of such networks. There is great work happening in this group and we’re looking forward to listening to the discussions.
Today at IETF 90 we on the Deploy360 team will be starting the day focusing on the “Internet of Things (IoT)” as we listen to what is being discussed in the 6LO working group. Formally titled “IPv6 over Networks of Resource Constrained Nodes” this group focuses on using IPv6 in low power and constrained environments such as sensor networks, “smart grids” and other embedded environments. The 6lo agenda is full of drafts exploring different types of such networks. There is great work happening in this group and we’re looking forward to listening to the discussions.
At the end of the scheduled working group sessions we’ll also be in IPv6-land as we join in the SUNSET4 Working Group looking at what needs to be done to ensure that networks can operate in the absence of IPv4, i.e. in an IPv6-only situation. Today’s SUNSET4 agenda looks at how to shut off IPv4 on a network and several drafts about how to work in an IPv4-only space.
At the same time as the SUNSET 4 WG there will also be the TLS Working Group that will be looking at several new encryption mechanisms for TLS.
In between those IPv6 and TLS sessions I’ll be sitting in the DNSSD working group. As I mentioned in the Rough Guide post relating to DNSSEC, the work in this group doesn’t directly apply to DNSSEC, but there are discussions relating to DNS security in general that are important for us to monitor.
Some of the other sessions that some of our team members may monitor include:
- 13:00-15:00 – Security Area Open Meeting
- 15:20-17:20 – Routing Area Open Meeting
- 15:20-17:20 – TCP Increased Security
If you’d like to join the 6LO or SUNSET4 sessions (or any of the others) remotely to hear the discussion you can follow the instructions on the IETF 90 Remote Participation page or use the “tools-style” agenda page that provides easy links to the audio stream, jabber chat room documents and more for each of the sessions.
Lunch Briefing About 5G Wireless Technology
In the middle of the sessions during the lunch break from 11:30-13:00 EDT I’m planning to be in Ballroom to listen to a presentation from Erik Dahlman of Ericsson about what “5G” technology is all about. The abstract is:
Discussions on fifth generation (5g) wireless access has rapidly intensified during the latest two years. 5G wireless access is seen as the long-term enabler of the overall networked society, not only providing enhanced mobile broadband access but being a tool to provide wireless connectivity for any kind of application.
This speech will provide an overview of the state of 5G efforts around the world. We will discuss the specific requirements and challenges being identified for 5G wireless access and the different technology
components and alternatives being considered. We will also outline possible time schedule for 5G in ITU and 3GPP.
The lunchtime session will have a live video stream and will also be recorded for later viewing.
Bits-N-Bites
We’ll be ending the day at the Bits-N-Bites session that has a new format and what look like very cool demonstrations related to the “Internet of Things”. Should be fun to see!
The information about the relevant working groups today is:
6LO (IPv6 over Networks of Resource Constrained Nodes) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/6lo/
Documents: https://datatracker.ietf.org/wg/6lo/
Charter: https://datatracker.ietf.org/doc/charter-ietf-6lo/
(Thursday, July 22, 2014, 0900-1130 EDT, Tudor 7/8)
DNSSD (Extensions for Scalable DNS Service Discovery) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/dnssd/
Documents: https://datatracker.ietf.org/wg/dnssd/
Charter: https://datatracker.ietf.org/wg/dnssd/charter/
(Thursday, July 24, 2014, 1520-1720 EDT, Canadian)
SUNSET4 (Sunsetting IPv4) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/sunset4/
Documents: https://datatracker.ietf.org/wg/sunset4/
Charter: http://tools.ietf.org/wg/sunset4/charters
(Thursday, July 22, 2014, 1730-1830 EDT, Tudor 7/8)
TLS (Transport Layer Security) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/tls/
Documents: https://datatracker.ietf.org/wg/tls/
Charter: http://tools.ietf.org/wg/tls/charters
(Thursday, July 22, 2014, 1730-1830 EDT, Ontario)
For more background on what is happening at IETF 90, please see our “Rough Guide to IETF 90″ posts on the ITM blog:
- Rough Guide to IETF 90: DNSSEC, DANE and DNS Security (see also our Deploy360 post on the topic)
- Rough Guide To IETF 90: IPv6 Is Everywhere, eh?
- ISOC Rough Guide to IETF 90: Routing Resilience
- Overview: ISOC Rough Guide to IETF 90: Toronto, Eh?
If you are here at IETF 90 in Toronto, please do feel free to say hello to a member of the Deploy360 team. And if you want to get started with IPv6, DNSSEC or one of our other topics, please visit our “Start Here” page to find resources appropriate to your type of organization.
Jul 24
What is "5G" Wireless Technology? Watch LIVE in 2 hours to learn more…
Discussions on fifth generation (5g) wireless access has rapidly intensified during the latest two years. 5G wireless access is seen as the long-term enabler of the overall networked society, not only providing enhanced mobile broadband access but being a tool to provide wireless connectivity for any kind of application.
This speech will provide an overview of the state of 5G efforts around the world. We will discuss the specific requirements and challenges being identified for 5G wireless access and the different technology components and alternatives being considered. We will also outline possible time schedule for 5G in ITU and 3GPP.
Given that so many people are getting their Internet access through mobile networks (and increasingly will be doing so in the future), I think it's extremely important to understand where these mobile technologies are going.
The speaker is Erik Dahlman from Ericsson and more information about his background can be found on the lunch session description page on the IETF website.
The presentation will be recorded and will be able to be viewed in the viewer below after the session is over. (And again, check the IETF Google+ event page for more information about the session and any updates.
UPDATE: Unfortunately Google's YouTube Live service when down for maintenance at the time we wanted to start our session:
Instead you need to watch the session on LiveStream.com at: http://new.livestream.com/internetsociety/IETF90
If you found this post interesting or useful, please consider either:
- following me on Twitter;
- adding me to a circle on Google+;
- following me on App.net
- subscribing to my email newsletter; or
- subscribing to the RSS feed
Jul 23
Deploy360@IETF90, Day3: Operators and the IETF, DHC, DANE in TRAM, CrypTech and more
 Wednesday at IETF90 is a bit quieter day for our Deploy360 topics, which is nice after the crazy schedule of yesterday and of Monday . It’s still quite busy and starts off with our team member Jan Žorž presenting in the OPS Area Working Group about our “Operators and the IETF” project, as well as IPv6 activity happening in the DHC Working Group. We learned of a new DANE draft happening in the TRAM Working Group. The CrypTech project has a lunch briefing and the Routing Area Working Group meets this afternoon. More info below…
Wednesday at IETF90 is a bit quieter day for our Deploy360 topics, which is nice after the crazy schedule of yesterday and of Monday . It’s still quite busy and starts off with our team member Jan Žorž presenting in the OPS Area Working Group about our “Operators and the IETF” project, as well as IPv6 activity happening in the DHC Working Group. We learned of a new DANE draft happening in the TRAM Working Group. The CrypTech project has a lunch briefing and the Routing Area Working Group meets this afternoon. More info below…
If you’d like to join the OPSAWG or TRAM sessions (or any of the others) remotely to hear the discussion you can follow the instructions on the IETF 90 Remote Participation page or use the “tools-style” agenda page that provides easy links to the audio stream, jabber chat room documents and more for each of the sessions.
OPS Area Working Group - and IPv6 in DHC
In the Operations Area Working Group from 9:00-11:30 EDT, Jan is going to be speaking about our “Operators and the IETF” project and presenting some preliminary results from the survey we undertook to understand what were some of the reasons network operators had for not participating in the IETF standards process. The goal here is to relay the feedback we’ve collected thus far and have a conversation about how we might be able to get more network operators involved with the IETF so that we can improve the amount of operational feedback provided into the standards process.
At the same time in another room the DHC Working Group will be covering a great many topics related to IPv6 and DHCP, specifically clarifying various points about how DHCP works with IPv6 and how to use DHCP more securely.
Lunch Briefing About The CrypTech Project
During the lunch break from 11:30-13:00 EDT in the Quebec Room there will be a briefing about the CrypTech Project, a fascinating project to develop an open hardware cryptographic engine. Our colleague Lucy Lynch recently wrote about this in a blog post, “The Black Box Paradox – How to Trust a Secret on Today’s Internet“. It looks quite interesting.
A DANE Draft in TRAM
In a side conversation with Marc Petit-Huguenin here at IETF 90 on Monday I learned that he has a DANE-related draft in the TRAM Working Group. The TRAM WG is focused on improving the TURN and STUN servers that facilitate real-time communications between people who are behind NAT boxes such as home / enterprise firewalls. This is particularly of interest to people working on WebRTC/RTCWEB. Marc’s draft, draft-petithuguenin-tram-stun-dane-00, defines how DANE can be used by STUN clients to secure the TLS connection with servers. His slides are available.
After that we’ll probably be in the Routing Area Working Group and then listening to the Operations and Administration Plenary tonight. And then we’ll be getting ready for another VERY busy day tomorrow!
The information about the relevant working groups today is:
DHC (Dynamic Host Configuration) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/dhc/
Documents: https://datatracker.ietf.org/wg/dhc/
Charter: https://datatracker.ietf.org/wg/dhc/charter/
(Wednesday, July 23, 2014, 0900-1130 EDT, Salon B)
OPSAWG (OPS Area Working Group) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/opsawg/
Documents: https://datatracker.ietf.org/wg/opsawg/
Charter: https://datatracker.ietf.org/wg/opsawg/charter/
(Wednesday, July 23, 2014, 0900-1130 EDT, Ontario)
TRAM (TURN Revised and Modernized) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/tram/
Documents: https://datatracker.ietf.org/wg/tram/
Charter: https://datatracker.ietf.org/wg/tram/charter/
(Wednesday, July 23, 2014, 1300-1130 EDT, Manitoba)
RTGWG (Routing Area Working Group) WG
Agenda: https://datatracker.ietf.org/meeting/90/agenda/rtgwg/
Documents: https://datatracker.ietf.org/wg/rtgwg/
Charter: https://datatracker.ietf.org/wg/rtgwg/charter/
(Wednesday, July 23, 2014, 0900-1130 EDT, Ballroom)
For more background on what is happening at IETF 90, please see our “Rough Guide to IETF 90″ posts on the ITM blog:
- Rough Guide to IETF 90: DNSSEC, DANE and DNS Security (see also our Deploy360 post on the topic)
- Rough Guide To IETF 90: IPv6 Is Everywhere, eh?
- ISOC Rough Guide to IETF 90: Routing Resilience
- Overview: ISOC Rough Guide to IETF 90: Toronto, Eh?
If you are here at IETF 90 in Toronto, please do feel free to say hello to a member of the Deploy360 team. And if you want to get started with IPv6, DNSSEC or one of our other topics, please visit our “Start Here” page to find resources appropriate to your type of organization.
Jul 22
Great news! New IPv6 Web Sites: NBC.com, NBCSports.com, UniversalSports.com
Very cool news in Comcast’s announcement today that they launched IPv6 support for:
Naturally I had to check… and sure enough, using the IPvFoo plugin for Chrome, there in the upper right of www.nbc.com…
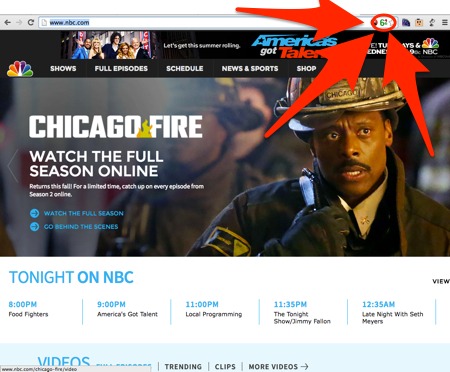
was the green “6″ showing it is connecting over IPv6:

Now, clicking on the green six in my browser bar will show that many of the sites that provide content into that web page are still IPv4-only, but it’s certainly a great start to have the main websites available over IPv6.
Kudos to the teams at Comcast and NBCUniversal for making this happen!

