December 2013 archive
Dec 09
TDYR #054 – On The Passing Of Nelson Mandela
Dec 09
FIR #733 – 12/9/13 – For Immediate Release
Dec 06
Want To Quickly Create A TLSA Record For DANE / DNSSEC?
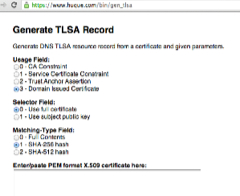 Would you like to use the DANE protocol to secure your SSL/TLS certificate via DNSSEC? If so, the first step is to generate and publish a “TLSA record” in DNS – and that record generation can be a stumbling block for some people. While there are command-line tools such as just the basic “openssl” or Paul Wouter’s “hash-slinger“, Shumon Huque recently released a web interface that lets you easily create a TLSA record. As Shumon writes about on his blog, the tool is at:
Would you like to use the DANE protocol to secure your SSL/TLS certificate via DNSSEC? If so, the first step is to generate and publish a “TLSA record” in DNS – and that record generation can be a stumbling block for some people. While there are command-line tools such as just the basic “openssl” or Paul Wouter’s “hash-slinger“, Shumon Huque recently released a web interface that lets you easily create a TLSA record. As Shumon writes about on his blog, the tool is at:
All you need to do is to set the type of TLSA record you want to create, paste in the X.509 certificate, and enter the appropriate port number, protocol and domain name. Shumon’s script then generates the appropriate TLSA record that you can paste into your DNS zone file.
Last year, Shumon wrote a post on “DNSSEC and Certificates” where he walked through how to do this using openssl on the command line – this latest post now builds on that to make it even easier.
It’s excellent that Shumon has made this tool available and we look forward to seeing many more TLSA records out there! (If you have a SSL/TLS cert for your website, how about adding a TLSA record today?)
The post Want To Quickly Create A TLSA Record For DANE / DNSSEC? appeared first on Internet Society.
Dec 06
Want To Quickly Create A TLSA Record For DANE / DNSSEC?
 Would you like to use the DANE protocol to secure your SSL/TLS certificate via DNSSEC? If so, the first step is to generate and publish a “TLSA record” in DNS – and that record generation can be a stumbling block for some people. While there are command-line tools such as just the basic “openssl” or Paul Wouter’s “hash-slinger“, Shumon Huque recently released a web interface that lets you easily create a TLSA record. As Shumon writes about on his blog, the tool is at:
Would you like to use the DANE protocol to secure your SSL/TLS certificate via DNSSEC? If so, the first step is to generate and publish a “TLSA record” in DNS – and that record generation can be a stumbling block for some people. While there are command-line tools such as just the basic “openssl” or Paul Wouter’s “hash-slinger“, Shumon Huque recently released a web interface that lets you easily create a TLSA record. As Shumon writes about on his blog, the tool is at:
All you need to do is to set the type of TLSA record you want to create, paste in the X.509 certificate, and enter the appropriate port number, protocol and domain name. Shumon’s script then generates the appropriate TLSA record that you can paste into your DNS zone file.
Last year, Shumon wrote a post on “DNSSEC and Certificates” where he walked through how to do this using openssl on the command line – this latest post now builds on that to make it even easier.
It’s excellent that Shumon has made this tool available and we look forward to seeing many more TLSA records out there! (If you have a SSL/TLS cert for your website, how about adding a TLSA record today?)
Dec 05
Can You Help With A Quick Survey About The ICANN DNSSEC Workshops?
 If you have ever attended – either in person or remotely – one of the DNSSEC Workshops that have taken place at ICANN meetings, could you please take just a couple of minutes to complete this survey about the workshops?
If you have ever attended – either in person or remotely – one of the DNSSEC Workshops that have taken place at ICANN meetings, could you please take just a couple of minutes to complete this survey about the workshops?
After a great DNSSEC Workshop at ICANN 48, the program committee (of which I am a member) is starting to plan for the next DNSSEC Workshop on March 26 at ICANN 49 in Singapore. As we do that planning, we’d really like to hear from participants about what they find most valuable in the workshops.
We’d particularly welcome any comments left in the open text box near the end of the survey. What else could we add to the workshops? Do you find them helpful as you go out and deploy DNSSEC? Is there anything we could do to make them better?
Please do let us know!
Thank you,
Dan (on behalf of the ICANN DNSSEC Workshops Program Committee)
Dec 05
Don’t Miss Friday’s Live VUC Call! – Martin Geddes on "Rethinking Broadband and Voice"
What are you doing tomorrow, Friday, December 6, 2013, at 12noon US Eastern (1700 UTC)? Would you like to join in to what should be an excellent conversation about the future of broadband networks, IP communications, telecom, etc.? If so, make plans to join the VoIP Users Conference (VUC) call happening live at 12 noon where the guest will be the ever-interesting Martin Geddes. The topic will be "Rethinking broadband and voice: Network Science and Hypervoice" and should prompt some vigorous discussion!
I've known Martin for many years now and have been a great fan of his analysis and writing ever since back in the days of his "Telepocalypse" blog. He's truly a great thinker in the space and is also quite an enjoyable and fun speaker to listen to. We know each other well from the early days of VoIP blogging as well as the conference circuit, and I regularly read his email newsletter and other great content he puts out. He's very active on Twitter as well.
Having said all that, I do have some fundamental disagreements with some of what he is advocating these days. I wrote about some of this disagreement last year and he and I had a good conversation both in the comments to that post and in some private exchanges.
Now, I very much agree with much of what he calls "Hypervoice" and where he sees voice going. Where we disagree is about the broadband component. This is the part that Randy outlines in the VUC page as:
He will outline some (controversial) answers that suggest we’re heading down a dead end and should consider a different technical and commercial approach.
It should be a fun conversation and I'm very much looking forward to the group discussion with Martin!
You can join the fun, too! If you want to just simply watch and listen, you can:
- view the event on the Google+ Hangout on Air Event page or on http://live.vuc.me (it will be both video and audio).
- listen to the audio stream only at Listen to MP3 stream at http://vuc.me/mp3
- Skype audio: +990009369991484768
- SIP:vuc@vuc.me
- PSTN (phone) international numbers: http://vuc.me/voxbone
Regardless of whether you are just listening or planning to participate, it's always a good idea to join the #vuc IRC channel on Freednode.net. More info and a web interface to IRC can be found on the VUC site.
If you can't join in live, the session will be recorded in both audio and video form. You'll be able to find the archive on the VUC page and on the Google+ event page.
Please do join us! It should be a great conversation!
If you found this post interesting or useful, please consider either:
- following me on Twitter;
- adding me to a circle on Google+;
- following me on App.net
- subscribing to my email newsletter; or
- subscribing to the RSS feed
Dec 04
TDYR #053 – Of Hard Drives, Space Gremlin And Native IPv6
Dec 03
Going Native IPv6 In My Home Office!
Today was a great day for me on a personal front – I finally have native IPv6 in my home office! I am no longer using an IPv6 tunnel!
To give some context, I live in the small city of Keene in the southwestern corner of New Hampshire, quite close to the neighboring U.S. states of Vermont and Massachusetts. For reasons dating back to a former cable system, our little city is a pocket of Time Warner Cable (TWC) customers while almost all the surrounding regions are Comcast customers. When I joined the Internet Society back in September 2011, one of the first things I did was contact TWC to see about getting native IPv6. Through some of the World IPv6 Launch work as well as IETF work I came to know some of the TWC staff and of course asked them, too. There’s a long story in there (a lot of which relates to being a small island of connectivity and apparently having older equipment that needed to be updated)… but in the meantime I was in fact getting IPv6 in my home office using an IPv6 tunnel via Hurricane Electric’s outstanding Tunnelbroker.net. Still, I’ve been wanting native IPv6 connectivity.
At IETF 88 in Vancouver last month Lee Howard of TWC told me that IPv6 had been turned on for Keene and that it should work when I got home. This week I finally had a chance to see if it could work. It didn’t… but some troubleshooting determined that the firmware needed to be updated in my cable modem. Once that was done and I made a few changes on my Linux-based home server/gateway, everything was in order and I was absolutely thrilled to be able to go to http://test-ipv6.com and get these results:
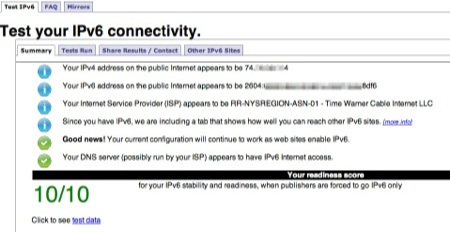
I’m now natively on the IPv6 Internet!
Given that I work on this Internet Society Deploy360 Programme and write here about IPv6 all the time, this is a rather important step for my little home office! Many thanks to Lee and his colleague Jason for their help. The good news, too, is that another techie friend of mine in Keene who is also a TWC customer learned of this news and he, too, is now working to make sure his home network works with IPv6. All good stuff!
Another outcome is that I realized that it would be really good to add to our list of IPv6 resources some focused tutorials on how to configure home server/gateway/router software to work with IPv6. I’m sure there are some good tutorials out there for some of the various packages… and where such documents don’t exist I would think they would be relatively straightforward to write for others. I’m going to write up what I did soon as an example… and then may be putting the call out there to others of you to see if we can get some other tutorials for different software packages.
Anyway, I’m doing a little IPv6 dance here in little, old Keene! Good times for an IPv6 advocate!
Dec 02
WMUR To Showcase Curling In NH At 7pm Tonight on NH Chronicle
 Tonight (Dec 2) at 7:00pm WMUR’s “New Hampshire Chronicle” will feature a segment on the growth of the sport of curling in New Hampshire. As they say:
Tonight (Dec 2) at 7:00pm WMUR’s “New Hampshire Chronicle” will feature a segment on the growth of the sport of curling in New Hampshire. As they say:
A new ice sport is gaining traction and you don’t need skates, just some heavy granite stones and a few brooms. Curling is becoming a popular sport and there is a club in Conway that is helping it catch on.
The segment is about the Mount Washington Valley Curling Club up on the opposite end of the state in Conway, NH. The MWVCC was formed in 2011 and curls at the Ham Ice Arena.
This is VERY cool to see and I encourage everyone who can to watch it to see about curling in New Hampshire! (And then let’s please join together to help bring curling to the Monadnock region!)
Dec 02
Afnic Publishes Issue Paper: “Securing Internet Communications End-to-end Using DANE Protocol”
 Last week, the great folks over at Afnic released an outstanding issue paper about how the DANE protocol and DNSSEC can bring a higher level of trust and security to Internet-based communications. The issue paper, “Securing End-to-end Internet communications using DANE protocol“, is available in PDF (direct link) and walks through how DANE can be used to increase the security used in TLS/SSL certificates (PKIX). The document describes the problems associated with the current world of certificates and then explains how DANE can make the situation more secure.
Last week, the great folks over at Afnic released an outstanding issue paper about how the DANE protocol and DNSSEC can bring a higher level of trust and security to Internet-based communications. The issue paper, “Securing End-to-end Internet communications using DANE protocol“, is available in PDF (direct link) and walks through how DANE can be used to increase the security used in TLS/SSL certificates (PKIX). The document describes the problems associated with the current world of certificates and then explains how DANE can make the situation more secure.
Readers of this Deploy360 site will know that we’ve produced similar types of documents ourselves, but not in an “issue paper” form that can be distributed. The Afnic folks have done a great job with this and I like the graphics they are using.
As they note on the final page, DANE is for much more than web browsing – and in fact the major implementations we’re seeing right now are in other services like email and XMPP (Jabber). The browser vendors have so far not seen enough requests (we are told) to look at including DANE in their browsers.
Hopefully this document from Afnic will help people further understand the very real value DANE can bring in ensuring that you are using the correct TLS/SSL certificate when you are connecting to a web site.
Kudos to the Afnic team for creating this document – and I encourage everyone to share this document widely! (Thanks!)

